Consider this an evergreen post as of 10/06/2020
Introduction
The purpose of this blog post to aim for a consistent modern authentication experience for employees when consuming Citrix Virtual Apps & Desktops (CVAD) + CVAD Service regardless of where the (CVAD) workloads are running, either in *Azure, *AWS, *GCP or *On-Premises. The primary priority is that the employees identity is owned and managed by a cloud identity platform e.g Azure Active Directory (AAD) and the employees identity within each resource location* for CVAD usage maps to AD shadow accounts. These AD shadow accounts represent the employee as a UPN e.g human.name@domain, with a RANDOM long complex password that the employee doesn’t need to ever know and all IT is required to do beyond creating a AD shadow account is then assign the right vs. relevant security privileges and access to CVAD including Policies meeting local, geo of industry compliance and governance while maintaining a great employee experience.
The second priority is that the employees device can frictionlessly access CVAD resources using either a Forward Proxy, SD-WAN Overlay Network or ICA Proxy. I do recognise that many organisations are still required to make use of a VPN style strategy at the current moment and therefore this solution can also work for those devices as well repurposing the existing Citrix Gateway to also support a Full VPN beyond ICA Proxy or you can use other well established and trusted VPN solution providers.
Leveraging a Bring Your Own “either Enterprise vs. Personal” Identity (ByoI) is a concept I ponded way back in 2017 and now feels like the right time to pick that up concept again during the current Workplace transformation happening all around the world due to world wide COVID-19 pandemic. Using a ByoI strategy as high level vision you can efficiently deploy CVAD to any *Azure, *AWS, *GCP region or *On-Premises with less friction and you don’t need to be worry about “Password Syncing” just replicate the employee’s UPN + AD Security Privileges + CVAD Access & Policies where its required. It has the added benefit if you want do mix and match public cloud workloads to avoid lock-in amongst other topics, you’ll be providing a common and consistent login interface + experience irrespective of where the workload is sat.
It another brilliant benefit is the on-boarding of 3rd Parties (3P’s) using ByoI concept with a business check at the edge, the 3P brings there owned Identity and in the current world we live in I don’t think that is bad thing it could even strength that employees individual security as there identity will be bound to a smartphone which knows more about your individuals habits and you that you know yourself. If we can unlock a co-shared responsibility identity model between the individual + organisation we can truly aim for a passwordless workspace that only uses virtual smartcards or tokens.
Finally the on-boarding of M&A employees can be faster as you can generate them a few days after commercial signing with a new brand identity that resides in Azure AD (or Google, OKTA e.t.c) whilst they continue accessing existing workplace apps + data with current AD credentials, IT + HR + Business can choose when to layer in the “NEW” Workspace Platform for Work from group perspective into the existing Workspace with less friction and complexity. Yes this final topic is complex when we think about merging different Business IT and IT Systems together, a CVAD strategy with FAS bridges the GAP reducing friction and complexity for IT to sun rise a new Workspace stack for that newly acquired organisation while sunsetting the exciting Workspace stack and those new M&A employees get to on-board beyond the Workspace into there new organisations people, its culture, vision and values and avoids the IP drain that often can easily happen.
The Employee Experience
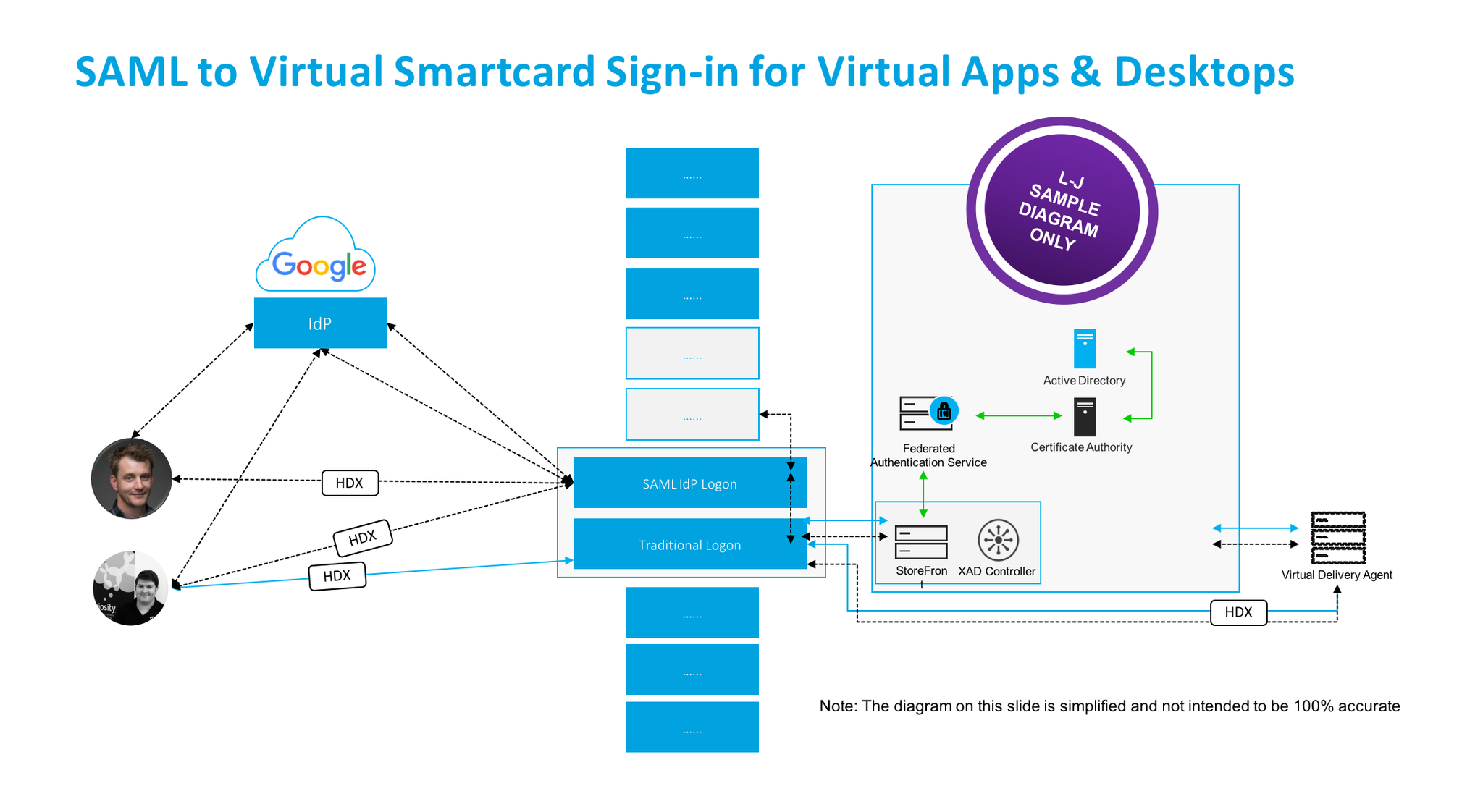
#AzureAD #SAML Sign-in with a Virtual Smartcard for @citrix Virtual Apps & Desktops enabling a consistent SSO experience when running workloads in #Azure #AWS #GCP On-Premises or in all of them. pic.twitter.com/38FDBLgNfJ
— Lyndon-Jon Martin 👨🏻💻 (@lyndonjonmartin) June 10, 2020
High Level Architecture
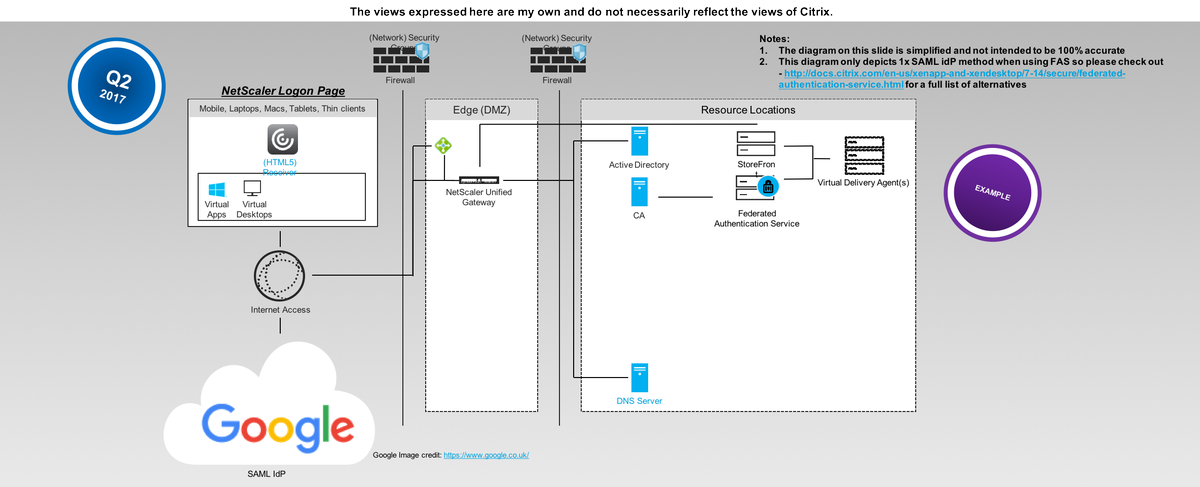
The scenario below depicts accessing a StoreFront server on any device type from within the Workplace fabric in any office locally or world wide or from a IT managed device that makes use of a Full VPN, Forward Proxy technology; WFH Citrix SD-WAN appliance where traffic passes over an SD-WAN overlay network; Citrix Endpoint Management enrolled smart device with per-app mVPN configured and finally irrespective of the devices management status you can use ICA Proxy* to access CVAD resources anywhere over the internet inclusive of any home via a Citrix ADC (formerly NetScaler) using the Gateway functionality which is “VPN-Less*”.
Architecture for using #AzureAD #SAML converted to a Virtual Smartcard to SSO onto @citrix Virtual Apps & Desktops enabling a consistent SSO experience when running workloads in #Azure #AWS #GCP On-Premises or in all of them. pic.twitter.com/DAt6MukmIO
— Lyndon-Jon Martin 👨🏻💻 (@lyndonjonmartin) June 10, 2020
Systems Requirements & Pre-requisites
1. A UAT or Test CVAD 1912 LTSR Site that already setup. My personal one runs in AWS EC2 as it retains hosting connections or public clouds to preform MCS provisioning of machines from customer own and managed control plane. You can also use the Citrix Virtual Apps & Desktops (CVAD) Service or sign-up at https://citrix.cloud.com/ and engage your local Citrix representatives to get a trial setup for the CVAD Service.
2. Deploy a new VM which will run the following Citrix 1912 LTRS StoreFront and Federated Authentication Service (FAS) roles to create a new “Store” on StoreFront called “AAD” which will be configured to accept the Azure AD SAML token which will then convert the AAD SAML tokens into a Citrix virtual smartcard to SSO the employee onto CVAD resources.
3. Install StoreFront – https://docs.citrix.com/en-us/storefront/1912-ltsr/install-standard.html after reading the system requirements – https://docs.citrix.com/en-us/storefront/1912-ltsr/system-requirements.html.
4. Setup and Configure FAS Role on your StoreFront Server – https://docs.citrix.com/en-us/federated-authentication-service/1912/install-configure.html after reading the system requirements carefully – https://docs.citrix.com/en-us/federated-authentication-service/1912/system-requirements.html, this part shouldn’t be a problem e.g leaning on on Security teams whom control the Enterprise CA Admins as you’ll hopefully be using a proper UAT or Test CVAD environment with all the Microsoft management servers and roles including an Enterprise CA which FAS requires and access to AD introduce new GPO’s.
5. An Azure AD “personal or business test” tenant.
Deployment Guide
Azure AD Setup & Configuration – Personal Home Lab Edition
If you have a separate Azure AD tenant in Azure you can proceed to the next section, however if you are an IT Pro that wants to test out how to convert Azure AD SAML logins to Citrix virtual smartcards for CVAD the following the below guidance below for setting up a personal ADD tenant with a personal Azure account for your home lab. WARNING I am not an Azure AD nor on-premises AD expert, therefor follow the leading practises found in Microsofts documentation for Azure AD.
1. Navigate to https://portal.azure.com and sign-in with your live vs. personal Microsoft account. Select “Create a resource”.
2. Select “Identity” then select “Azure Active Directory”.
3. Enter in an “Organisation Name, Initial domain name and select your Country or region”.
4. The wizard will begin creating your AAD tenant .
5. Once it completes click the hyperlink within “Click here to manage your new directory”.
6. At the Overview page of your new AAD tenant select “Users” under “Manage” section.
7. Select “+ New user” under the “All Users (Preview)” Overview you’ll notice your personal email addr.
8. You’ll notice when creating a new employee account for your AAD tenant that you can only append domain.onmicrosoft.com to the username, I’ll explain how-to convert that to user@domain and remove the UPN requirement of user@doamin.onmicrosoft.com in the next few steps. For now fill the following fields “User name”; “Name”; “First name”; “Last name”; “Password” (choose or auto-generate) and the select “Create” keeping the defaults as they are.
9. Your new AAD employee is successful created, you can assign roles. NOTE for my personal testing purposes I didn’t configure anything as I’ll delete that test employee AAD account after my testing.
10. At this point I’m not going to deploy nor setup the “Azure AD Connect” in my Citrix Cloud Resource Location as I want the employees primary identity to always reside in Azure AD as the single source of truth, and then bring that identity to my Citrix Cloud Resource Location e.g Bring your own Identity (ByoI) and after a successful AAD SAML login map that to a hardened AD Shadow account with long complex password that the employee will never know and all I need to do it assign the AD security privilege and access for CVAD resources. This approach means that employee will NEVER enter in a AD password within a Citrix Cloud Resource Location that is configured for AAD (or Google, OKTA e.t.c) when using CVAD 1912 LTSR StoreFront and the Federated Authentication Service (FAS) in a Resource Location(s). For complex environments yes you’ll likely deploy the “Azure AD Connect” software as a role somewhere to replicate the employees but you don’t need to replicate there passwd or you can provision the employee twice once in AAD as in the example above and then again manually in AD in the Resource Location as there corresponding AD shadow account which matches the UPN from AAD when authenticating using SAML to StoreFront, the choice is yours but I found for testing purposes a manual in each is far less frictionless.
On-Premises Active Directory (AD) within your Resource Location
1.Create a new AD “Shadow” account that matches the “User Principal Name (UPN)” in AAD e.g user@domain, generate a random long complex password which they don’t need know and then assign or inherit the right vs. relevant AD security groups, GPOs that you would usually assign to a CVAD consumer.
2. On-board your domain into Azure AD which required verifying it with a MX record to avoid using user@domain.onmicrosoft.com so that you can use user@domain keeping it simple and less complex.
Installation and Configuring the Federated Authentication Service (FAS)
1. On the new VM that you just installed 1912 LTSR StoreFront role onto from the existing mounted ISO run the autorun splash screen and select “Federated Authentication Service”.
2.Read the EULA which you’ll need to “Accept the Licenses Agreement” to continue.
3. Accept the defaults and select “Next” on the “Core Components” page.
4. Accept the defaults and select “Next” on the “Firewall” page.
5. Once the installer is finished select “Finish” to close.
6. Open a PowerShell window in Admin mode then copy & paste the following code below, which will enable a trust between the CVAD Controller and the StoreFront server, minimise this window you’ll require it later.
Set-BrokerSite -TrustRequestsSentToTheXmlServicePort $true
7. Navigate to the following path “C:\Program Files\Citrix\Federated Authentication Service\PolicyDefinitions\” on the current StoreFront server that you installed FAS role onto, copy the following two files “CitrixFederatedAuthenticationService.admx” and “CitrixBase.admx” the entire folder “en-US” to a network share which will need to be accessible from your Windows Domain Controller or WDC.
8. Connect to your Windows Domain Controller (WDC) via RDS from the current StoreFront + FAS server and copy the two *.admx FAS files including folder “en-US” from your network share to the following path on the “C:\Windows\PolicyDefinitions” on your WDC.
9. Open an “MMC” console and load the “Group Policy Management Editor” snap-in, at the prompt for a Group Policy Object, select “Browse” and then select ”Default Domain Policy”.
10. In the MMC console navigate to “Default Domain Policy [server name] > Computer Configuration > Policies > Administrative Templates > Citrix Components > Authentication” and you should see the following three policies available “Federated Authentication Service”, “StoreFront FAS Rule” and “In-session Certificates”.
11. Select and open the “Federated Authentication Service” policy, next select to “Enable” it followed by selecting the “Show” button parallel to “DNS Addresses” label and enter in the FQDN e.g. “server.domain” of your StoreFront + FAS server and then select “OK” and then select “OK” to save the policy configuration and enabling FAS.
12. Next select and open “In-session Certificates” and select “Enabled” and in the “Consent timeout (seconds):” field type in a value of “30” which is the default.
13. Next close the MMC console and open up the existing PowerShell (Admin mode) and copy and paste the following code to force a Group Policy Update.
gpupdate /force
14. Minimise the RDS connection from your WDC so that you are back on your StoreFront + FAS server. Search and open up Citrix FAS in Admin mode, if you don’t you will be notified in the UI and then select “run this program as administrator” which will reload the FAS UI in Admin mode.
15. Select to “Deploy” for “Deploy certificate templates”.
16. Select “Ok” on the pop-up window that appears.
17. You’ve now successfully deployed the certificate templates, now select “Publish” for “Set up a certificate authority”.
18. Select the right Enterprise Certificate Authority (CA) from the available list and select “Ok”.
19. You’ve now deployed the certificate templates successfully to your Enterprise CA, now select “Authorize” for “Authorize this service”.
20. Select the right Enterprise Certificate Authority (CA) from the available list (same as above) and select “Ok”.
21. The FAS UI will display a spinning icon as the authorisation request is pending on the Enterprise CA server.
22. Connect to your Enterprise CA via RDS and the “Microsoft Certification Authority” MMC Console and navigate to “CA > CA Server > Pending Requests” you’ll see pending certificate right click it select “All Tasks > Issue” and the certificate will be issued.
23. Verify the issues certificates are issued by selecting “Issued Certificates” and verify you can see two issues certificated that begin with “Citrix_RegistrationAu…”.
24. Minimise your RDS session to your Enterprise CA and return to the StoreFront + FAS server, you now notice the “Authorize this service” says “Reauthorize” which is correct as the FAS service is now authorised with the Enterprise CA. Next select “Create” for “Create a rule”, which launch a new window.
25. Accept the default “Create the default rule (recommended)” and select “Next”.
26. Accept the default “Citrix_SmartcardLogon (recommended)” and select “Next”.
27. Select the previously selected and configured Enterprise CA you Authorised and select “Next”.
28. Select “Allow in-session use” and select “Next” if you enabled the following policy “In-session Certificates” earlier.
29. Select “Manage StoreFront access permissions (access is currently denied)” in red text which will open a new window.
30. Remove “Domain Computers” and add the “Server” running the StoreFront + FAS roles and under “Permissions” to “Allow” then select “Apply” and “Ok”.
31. The screen will update with “Manage StoreFront access permissions” to now be in blue text, now select “Next”.
32. Select “Manage user access permissions (all users are currently allowed)” in red text which will open a new window.
33. You can change to default “Domain Users” to your own test AD security group, then under “Permissions” to “Allow” then select “Apply” and “Ok”.
34. The screen will update with “Manage user permissions (all users are currently allowed)” to now be blue text, now select “Manage VDA permissions (all VDAs are currently allowed)” which is in red text.
35. You can change to default “Domain Computers” to your own test AD security group that your Citrix Virtual Delivery Agents (VDA) are found within, then under “Permissions” to “Allow” then select “Apply” and “Ok”.
36. The screen will update with “Manage VDA permissions (all VDAs are currently allowed)” to now in blue text, now select “Next”.
37. Now select “Create” and a “Default” FAS rule.
38. You have now successfully setup and configured Citrix FAS, you still need to enable FAS Claims for your “AAD” store on StoreFront which is covered later in this blog post.
Creating a new Store call “AAD” for Azure AD SAML Authentication in StoreFront
1. Open Studio and select “StoreFront” then select “Stores” and the on the “Actions tab” select “Create Store”.
2. On the splash screen select “Next“.
3. Type in “AAD” for the “Store Name” field and click “Next”.
4. Select “Add” list a CVAD controller, a new window will appear where you need provide the following information a “Display Name” e.g Citrix Cloud Connectors vs. CVAD 1912 LTSR, for the “Type” select “Citrix Virtual Apps and Desktops” and under “Servers” list select “Add” and type in the Citrix Cloud Connector or CVAD 1912 LTSR addresses and choose “Transport type” either HTTP 80 or HTTPS 443 (Preferred) and click “OK”.
5. You are now returned to the “Delivery Controller” page with a list of either Citrix Cloud Connectors or CVAD Controllers 1912 LTSR, click “Next“.
6. Now on the “Configure Authentication Methods” page select “SAML Authentication” and leave “User name and password” checked as YES, then click “Next”.
7. Ignore “Remote Access” configuration and click “Next“. NOTE: I will update this blog post at a later date with the Remote Access via Citrix Gateway formerly NetScaler Gateway.
8. Accept the default’s on the “Configure XenApp Services URL” and click “Create”.
9. StoreFront will begin creating your new “AAD” Store on your StoreFront server, once the wizard completes select “Test Site” to verify you can see a webpage that displays Citrix Receiver or you can navigate to “https://FQDN/Citrix/AADWeb/” replacing the FQDN with your own to verify the webpage is available.
Generating AAD SAML Configuration for StoreFront
1. In the Azure AD UI in the Azure Portal select “Enterprise applications” node.
2. When the UI updates in the centre select “Select “New application”.
3. You are taken to the “Add an Application” wizard and presented with three options select “Non-gallery application“.
4. Next provide a name for your own application e.g AAD-SAML-CVAD1912LTSR and then click “Add” at the bottom.
5. The AAD wizard completes and you are taken to the “Overview” page for “AAD-SAML-CVAD1912LTSR“, now select “Users and groups” from within this view.
6. Add an native AAD user(s). Note do not add any employee that does not have a AD shadow account setup and configured in the Citrix Cloud Resource Location (RL).
7. Now from the same “Overview” page for “AAD-SAML-CVAD1912LTSR” select “Single Sign-on” and on the “Select a single sign-on method” wizard select “SAML” and will start the AAS SAML wizard.
8. Select the pencil icon for “Basic SAML Configuration” to configure the following fields as follows below and select “Add“.
Identifier (Entity ID): https://FQDN/Citrix/AADAuth
Reply URL (Assertion Consumer Service URL):https://FQDN/Citrix/AADAuth/SamlForms/AssertionConsumerService
Sign on URL: https://FQDN/Citrix/AADWeb
9. Check under “User Attributes & Claims” portion that the “Name” field is configured to “user.userprincipalname”.
10. Scroll to “SAML Signing Certificate” and click to download the “Federation Metadata XML” e.g. AAD-SAML-CVAD1912LTSR.xml, now save or transfer it to your StoreFront server at C:\Temp.
Create and Configure a Azure AD SAML Trust in StoreFront
1. If you have transferred the *.xml file e.g “AAD-SAML-CVAD1912LTSR.xml“, then on your StoreFront server create a folder called “Temp” on “C:\” and transfer the downloaded *.xml file.
2.Open PowerShell in admin mode or launch it from Studio 1912 LTSR. Copy & paste the following code below, however if opening the PowerShell with Admin privileges without Studio 1912 LTSR then copy & paste this cmdlet first before proceeding with the configuration & “$Env:PROGRAMFILES\Citrix\Receiver StoreFront\Scripts\ImportModules.ps1“. You will notice the virtual path for the Store is already set here to AAD so you can copy and paste it as is. This code sets up and configures SAML for the ADD Store.
$storeVirtualPath = “/Citrix/AAD”
$auth = Get-STFAuthenticationService -Store (Get-STFStoreService -VirtualPath $storeVirtualPath)
$spId = $auth.AuthenticationSettings[“samlForms”].SamlSettings.ServiceProvider.Uri.AbsoluteUri
$acs = New-Object System.Uri $auth.Routing.HostbaseUrl, ($auth.VirtualPath + “/SamlForms/AssertionConsumerService”)
$md = New-Object System.Uri $auth.Routing.HostbaseUrl, ($auth.VirtualPath + “/SamlForms/ServiceProvider/Metadata”)
$samlTest = New-Object System.Uri $auth.Routing.HostbaseUrl, ($auth.VirtualPath + “/SamlTest”)
Write-Host “SAML Service Provider information:
Service Provider ID: $spId
Assertion Consumer Service: $acs
Metadata: $md
Test Page: $samlTest “
3. Next copy and paste the following code which will ingest SAML configuration from the Azure AD *.xml that you downloaded earlier and copied to C:\Temp on the StoreFront server.
Get-Module “Citrix.StoreFront*” -ListAvailable | Import-Module
# Remember to change this with the virtual path of your Store.
$StoreVirtualPath = “/Citrix/AAD”
$store = Get-STFStoreService -VirtualPath $StoreVirtualPath
$auth = Get-STFAuthenticationService -StoreService $store
Update-STFSamlIdPFromMetadata -AuthenticationService $auth -FilePath “C:\Temp\AAD-SAML-CVAD1912LTSR.xml”
4. Validate there are not error(s) on screen that need resolving.
5. Minimise your PowerShell window you’ll need it again shortly, now open up Studio or StoreFront MMC console and navigate to the “Stores” and select “AAD” and select “Manage Authentication Methods“.
6. Select the cog icon parallel to “SAML Authentication” and then select “Identity Provider” you should see that your AAD SAML configuration is setup and configured, leave it as is DO NOT TOUCH it!
7. Close all windows including Studio or StoreFront.
Enabling FAS for Converting Azure AD SAML Tokens to Virtual Smartcards
1.Open up your existing PowerShell window and copy and paste the following code below, which will ENABLE FAS for your ADD Store to convert AAD SAML tokens received into virtual smartcard that will be used to SSO the employee onto his/her Citrix virtual app and or desktop. You’ll notice the code is configured for the “AAD” Store so you can copy and paste as is.
Get-Module “Citrix.StoreFront.*” -ListAvailable | Import-Module
$StoreVirtualPath = “/Citrix/AAD”
$store = Get-STFStoreService -VirtualPath $StoreVirtualPath
$auth = Get-STFAuthenticationService -StoreService $store
Set-STFClaimsFactoryNames -AuthenticationService $auth -ClaimsFactoryName “FASClaimsFactory”
Set-STFStoreLaunchOptions -StoreService $store -VdaLogonDataProvider “FASLogonDataProvider”
2. Validate there are not error(s) on screen that need resolving, if there are none you can nose close the PowerShell window.
Testing your Azure AD SAML to Virtual Smartcard Login
1. Navigate to https://FQDN/Citrix/AADWeb which will redirect you to a AAD login.
2. Enter in your UPN e.g user@domain and then complete the required 2FA vs. MFA requirements setup by your organisation as requirement onscreen.
3. You will be returned to https://FQDN/Citrix/AADWeb and SSOed onto UI, depending on your setting your desktop will either auto launch of you’ll have to manually launch it yourself. The initial login will take slightly longer than usual as its generating you that initial virtual smartcard between StoreFront, FAS, AD and your Enterprise CA.
4. Your Citrix vDesktop or vApp should launch successfully and SSO the on without prompting for any credentials.
Troubleshooting
1.If you receive ANY error once returned to https://FQDN/Citrix/AADWeb post the AAD SAML login open a new browser tab in the same session and copy and paste the following URL https://FQDN/Citrix/StoreAuth/SamlTest to see if you have any oblivious errors e.g user@domain.onmicrosoft.com from Azure AD which doesn’t map to the AD Shadow account that is user@domain so its a UPN mismatch and the sign-on will continue to fail.
2. If the employee can sign on to https://FQDN/Citrix/AADWeb and the Citrix vApp or vDesktop launches but they see a credential prompt with “Other User” check and see that you configured FAS for the correct Store with SAML Authentication setup and configured if not using my example of “AAD” as the Store setup and configured on StoreFront.
ICA Proxy Remote Access with Azure AD SAML
Coming…
Concept on Bring your own Identity (ByoI) Strengthening Security through Co-Shared Responsibility owned by IT with different operating models
Its a simple concept which I like and yes it adds in complexity but it times today its far better to harden against unwanted 3rd party access whilst making it harder to achieve lateral movements. If the employee’s account is compromised by a 3rd party, they would need to compromise the employees identity in the cloud directory e.g AAD and in Active Directory (AD) on-premises as both passwords are completely different with different types of multi-factor authentication methods bound including access privileges.
Conceptual Bring your own Identity (ByoI)- Strengthening #Security through Co-Shared Responsibility owned by IT with different operating models WITHOUT PASSWORD SYNCING. pic.twitter.com/8XLt0wM19U
— Lyndon-Jon Martin 👨🏻💻 (@lyndonjonmartin) September 9, 2020
The views expressed here are my own and do not necessarily reflect the views of Citrix.