What is “Affordance”? It’s Design Thinking terminology summarised as follows – you can look at a product or service and visualise in your mind how it works a great example is of this is the play ▶️ and stop 🛑 buttons you can use these to interact with a product or service to start or stop the action, interactivity or stream.
Another example is volume controls on car radio its usually round nob and to turn the volume up you turn the round nob clock wise and the reverse to lower the volume.
Now that you have a simple understanding of what I mean by affordance let’s get started.
We live in an age of a complex technology spectrum, that is suppose to remove friction and barriers for employees but its actually in many instances making it worse, to achieve more while in some cases through people cultures at companies its driving productivity trends in the wrong direction inclusive of negative affect’s on employee (human) well-being. A recent “The Economist” article puts the remote workforce working up to a 30% more during the pandemic yet there are productivity inefficiencies, the link to the article is available at – https://www.economist.com/business/2021/06/10/remote-workers-work-longer-not-more-efficiently.
How does Citrix aim solve some of that complexity in the technology spectrum? It embraces the power of Affordance enabling employees (humans) to work on there own terms to achieve more in meaningful ways through flexible work-styles. Today many talk about a hybrid workforce, its staple founding principle upon which Citrix was built upon and its in its DNA with over 30 years of tenure enabling the hybrid operating model between the physical workplaces, at home or somewhere in between with different marketing lines my favourite – Work is not a place.
I know invite you to watch the following 3 minute demonstration where I’ll take a vanilla windows endpoint and I’ll enable Signal Sign-On (SSO) to a Software-as-a-Service (SaaS) web apps in my example i’ll SSO to Salesforce in several ways to demonstrate the Affordance of Citrix enabling employees (humans) to work on there own terms on any endpoint.
Demonstration of the Employee Affordance powered by Citrix
In the video you see a Windows endpoint that doesn’t having access to Salesforce that’s because it’s a SaaS web app and you typically access those types of apps using your web browser not via the Start Menu on a Windows endpoint or the Dock on Mac OS X.
Once the employee completes a sign-in to Citrix Workspace much like the Netflix app on your smart TV it provides you with recommendations; access to stream either movies, TV series of documentaries and in Citrix Workspace app it allows access to stream different web, SaaS and micro apps with SSO enabled so its seamless.
The difference between the Netflix and Citrix Workspace apps is that the Citrix Workspace app (CWa) supports different affordance in how a employee (human) may want to work vs. how IT and security teams determine the “How” employee (human) consume these apps – local, sandboxed, traffic reflection or a combination inclusive of security depth in by enforcing session watermarking, restrictions on cut, copy, paste and printing e.t.c
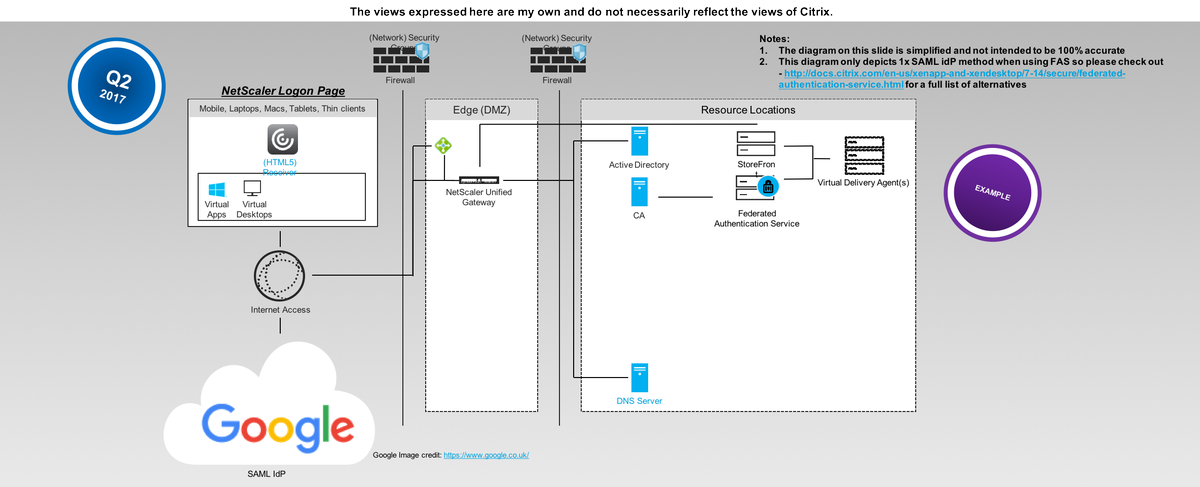
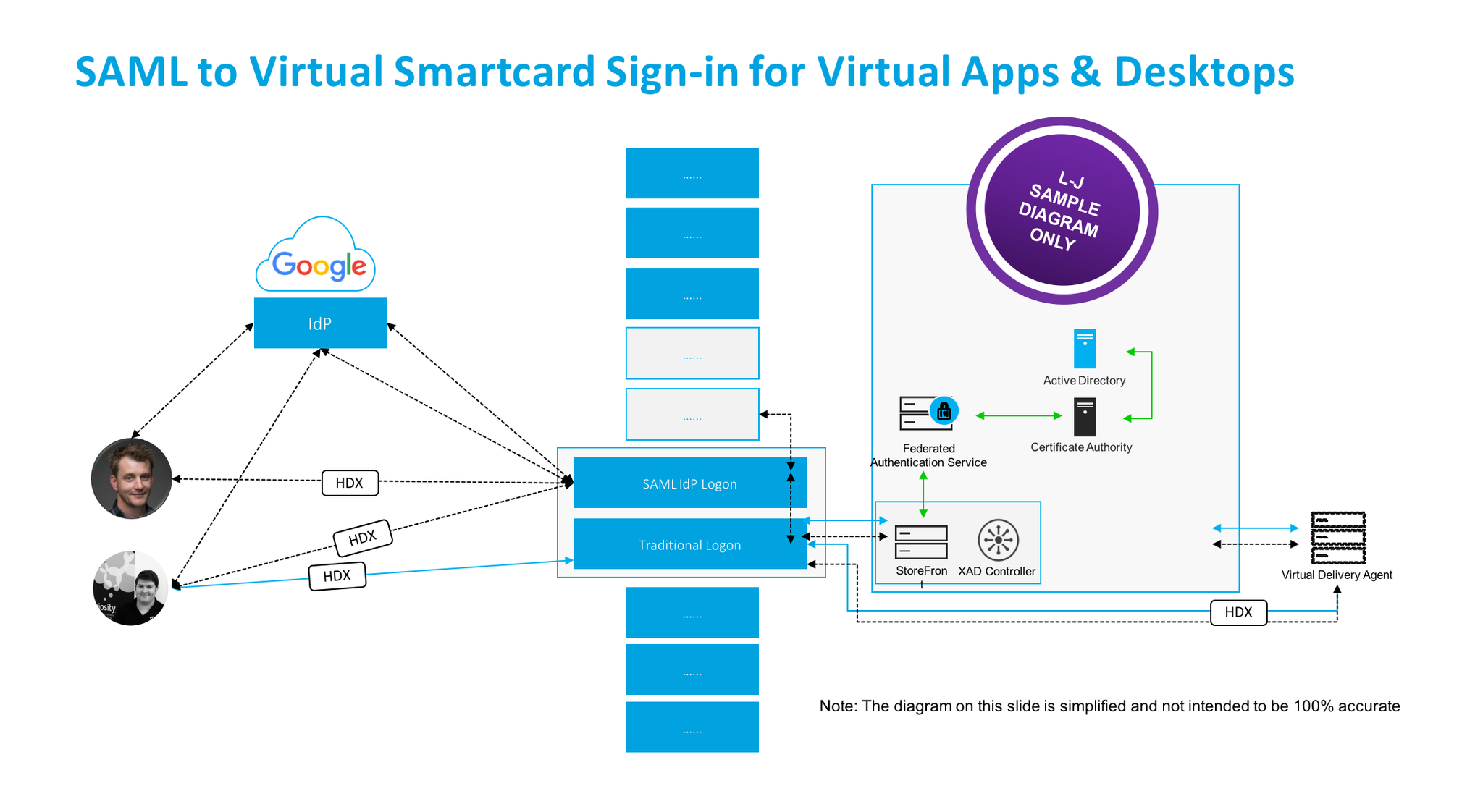
I know invite you to study the below hand drawn diagram, to make the experience hopefully more personal. The diagram depicts the entire demonstration above and how the flow of traffic and data is controlled and how contextual security access can be applied to different web, SaaS and micro apps using cloud native turn-key Citrix Cloud Platform services.
Time line of the Demo
Time 0 min 0 seconds
The Citrix apps has already been installed onto the employee (human) endpoint, this could be achieved by using Citrix’s own Endpoint management service vs. another or alternatively by some other legacy/traditional means e.g Domain joined endpoint using a full device VPN.
Time 0 min 13 seconds
On-board employee (human) + endpoint with Citrix Workspace for modern secure data, web & SaaS app delivery with SSO.
Time 0 min 29 seconds
Once Citrix Workspace app (CWa) is signed and is beginning to retreive and layer in the right and relevant SaaS, Web, (Virtual Apps & Virtual Desktops – optional) with Windows Start Menu or Mac OS X Dock integration by entitlement by job role vs. Business function. You will notice that while CWa is initializing there is NO Salesforce in the Windows start menu.
Time 0 min 55 seconds
Citrix Workspace app (CWa) enables a effortless Single Sign-On (SSO) experience using a magic token to SSO the Citrix Files app to gain access to the employees (humans) Cloud “My Docs” managed by Citrix or allows access to OneDrive for Business, Google Drive, Box, Dropbox e.t.c – Note the employee will need to sign-in only once to any of these Enterprise File Sync and Share (EFSS) platforms to then allow CWa to SSO the employee (human) to any of these EFSS platform which IT can control and allow access to.
Time 1 min 26 seconds
CWa has layered in all the employees (humans) web and SaaS apps into the Windows Start Menu, which the human can now search for and launch with just in time security and SSO after the click on the icon.
There are two version in this demo Salesforce and Salesforce Secure this is to show the different types of contextual security that can be enforced or ON vs. OFF at app vs. network latitudes.
Citrix Workspace affordance enabling frictionless access including SSO to SaaS e.g. Salesforce via Windows Start Menu integration launching the preferred native local endpoint with the browser traffic protected by Citrix Secure Internet Access (SIA) Service and the SSO to Salesforce is handed by the Citrix Gateway Service configured by IT for SSO e.g SAML.
When accessing Salesforce even though IT has turn OFF all app security enforcement policies at the OS and presentation layer e.g what the human sees and interacts with e.g Start Menu and Chrome Browser so its a native experience, the Citrix SIA Service is capturing and redirecting all the network traffic prior to traversing the endpoints network interfaces and forcing the traffic to a centralised Citrix SIA service tenant in the Citrix Cloud Platform that allows for IT and Security teams to enforce just in time cloud network security policy adds/moves/changes in near to real-time all without impacting and employee affordance by avoiding pushing down any type of update/patch/upgrade software package.
Time 1 min 48 seconds
Citrix Workspace app inclusive of the web browser portal version allows employees to use the Citrix Universal Search to search for web, SaaS apps and content from within the portal if this is how they choose to work and then access the same Salesforce SaaS app with the same SSO and network security enforced when using the CWa.
Time 1 min 57 seconds
In this example searching and starting the Salesforce Secure SaaS app and in this example IT has turned ON all the app security enforcement policies at the OS and presentation layers to add further depth and breathe avoiding any IP, Pii exfiltration and more.
When app security polices for web, SaaS apps are configured, then depending upon how the employee (human) intends to access his/her web, SaaS apps e.g Salesforce Secure it will make a decision based upon the individual employees (humans) preffered Affordance access method how to securely deliver Salesforce Secure e.g at 2 min 29 seconds you’ll see that its open, SSOed, running in a local sandboxed browser that is session watermarked with cut/copy/paste and printing denied or disabled between the sandbox and endpoint.
Time 2 min 44 seconds
What if the employee (human) decides actually I am going to bypass all of Citrix’s security policies and governance? We’ll guess what that just in time at a network level protected by Citrix SIA Service will intercept and enforce app security policies, in the example I open a new tab navigate to Salesforce type in my tenant and attempt to sign-in outside of Citrix Workspace app and bypass all that security, the Citrix SIA Service intercepts the request between endpoint (source) and destination (https://<tenant>.my.salesforce.com and recognises that method requires a remote browser isolation session to avoid and de-risk IP, Pii exfiltration and lateral movements. IT can choose to enforce or allow cut/copy/paste and printing from these remote browser isolation services that are intercepted by the Citrix SIA Service.
DT Architecture Diagram
What services where used to achieve this experience?
Secure Internet Access – https://www.citrix.com/products/citrix-secure-internet-access/
Secure Private Access (formerly Access Control and Secure Workspace Access) –https://www.citrix.com/products/citrix-secure-private-access/
Secure Browsing Service – https://www.citrix.com/products/citrix-secure-browser/
Citrix Analytics for Security – https://www.citrix.com/products/citrix-analytics-security/
All of these services are turn-key S/PaaS in nature powered by the Citrix Cloud Platform – https://citrix.cloud.com/ and have good IT Affordance meaning they aren’t difficult to setup, configure and manage, you’re talking about handful or minutes or a few hours to get a Minimal Viable Product or Prototype (MVP) into your employees (humans) hands to test and provide you with insights and feedback to refine your MVP.
The views expressed here are my own and do not necessarily reflect the views of Citrix.