The following content is a brief and unofficial prerequisites guide to better understand NetScaler Gateway Service from Citrix Cloud test delivering virtual apps and desktops powered by XenApp & XenDesktop Service prior to deploying in a PoC, Pilot or Production environment by the author of this entry. The views, opinions and concepts expressed are those by the author of this entry only and do not necessarily conform to industry descriptions or best practises. The views expressed here are my own and do not necessarily reflect the views of Citrix.
Shortened Names
NETSCALER GATEWAY SERVICE – nsg service or ngs
CITRIX CLOUD CONNECTOR – connector
NETSCALER – ns
HIGH-AVAILABILITY – h/a
XENAPP – xa
XENDESKTOP – xd
XENAPP/XENDESKTOP – xad
VIRTUAL DELIVERY AGENT – vda
HIGH DEFINITION EXPERIENCE – hdx
CITRIX CLOUD – cc
INFRASTRUCTURE AS A SERVICE – iaas
VIRTUAL APPLIANCE – vpx
USER EXPERIENCE – ux
ICA PROXY – hdx proxy
Introduction & Overview
The NetScaler Gateway Service is a simple, clean. effortless and but most importantly a powerful way to demonstrate the power of Citrix Cloud by providing secure remote access to your HDX virtual apps and desktops from your resources location over the internet (https) securely. While this service is very very powerful & simple to implement and use, you should under the keep in-mind that NS VPX/MPX/SDX is fully featured vs. the NSG Service which is focused on delivery of HDX virtual apps & desktops! So in summary when implementing service undering what is right vs. relevant for the customer needs and requirements is very important. Finally you can read more about the service and its benefits at https://www.citrix.com/products/citrix-cloud/services.html.
+Enabling the NetScaler Gateway Service
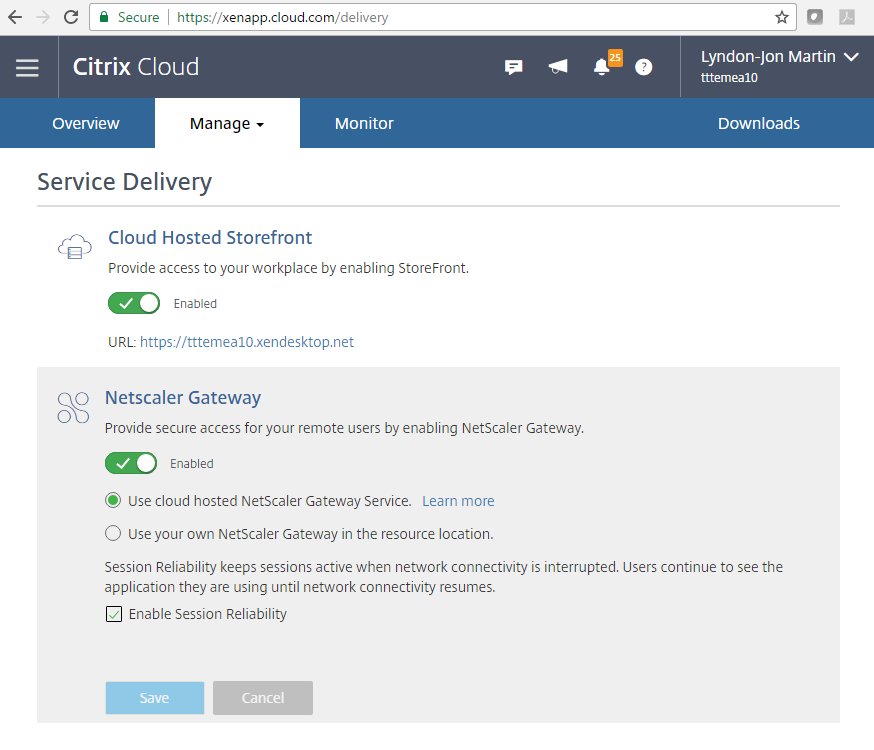
1. Login to https://citrix.cloud.com
2. Select to Manage your XAD Service which will take you to https://xenapp.cloud.com/.
3. Select from the drop down menu “Service Delivery” which is beneath the top menu item displayed “Service Creation”
4. Now Select to toggle “ON” and choose to use the NSG service (preferred for blog article only) or your own NetScaler (Unified) Gateway at your resource location and if you enable to the NSG Service you can choose to check the session reliability (2598) checkbox.
The UX
Users connect to https://
HDX Traffic flow of the NSG Service
Please note that traffic flow is based upon the diagram avaiable at – http://docs.citrix.com/en-us/citrix-cloud/xenapp-and-xendesktop-service/netscaler-gateway-as-a-service.html as of Jan 2017.
1. User MUST login into cloud hosted StoreFront e.g https://
2. Once the user has authenticated successfully he/she can select to launch a virtual app or desktop.
3. User connects to the NSG Service powered by Citrix Cloud
4. Traffic is securely brokered to the Connector in your resource location that is severing up the user’s selected virtual app or desktop or both from the server or desktop VDA.
Tech Overview of the NSG Service
1. The Citrix Cloud NetScaler Cloud Gateway service on your Connector allows and provides the secure remote access feature of the NSG Service from your chosen resource location. I have written a blog article about the Connector services and leading best practises which you can read at – http://axendatacentre.com/blog/2017/01/27/understanding-the-citrix-cloud-its-services-architecture-connectors/.
2. To ensure high availability you should always deploy at a min a pair of Connectors within your resource location and increase the compute capacity of your Connectors as user demand increases initially and thereafter deploy another Connector based upon usage of service.
3. *To use the NSG Service you MUST configure to use the cloud-hosted StoreFront provided by Citrix Cloud under “Service Delivery” tab at https://xenapp.cloud.com/delivery.
4. The NSG Service only supports HDX Traffic only and the service is currently only available on Eastern, Western coasts within the USA and in Europe so for those users accessing virtual apps and desktops via the NSG Service outside of these geos or not in close proximity to an entry point will experience higher latency so tweak your HDX policy(s)+ accordingly or deploy a NS VPX in your resource location.
5. ICA files are STA signed the below example is a small snippet from my own PoC and testing*. I have also intentionally scrammed some of the unreliable text to :-).
| Sample ICA file |
|
My Azure vDesktop $S19-38] Address=;40;CWSSTA;9D09CE5552BDE4581E888CD87EEEEFC AutologonAllowed=ON BrowserProtocol=HTTPonTCP CGPSecurityTicket=On ClearPassword=5FFE184444B0A0 ClientAudio=On ConnectionBar=1 DesiredColor=8 DesiredHRES=4294967295 DesiredVRES=4294967295 DesktopRestartAllowed=1 Domain=\78034E8888586B61 |
The NSG Service currently does not support and or is limited as of writing this blog article in Jan 2017 and based upon the embedded Twitter image – http://docs.citrix.com/en-us/citrix-cloud/xenapp-and-xendesktop-service/netscaler-gateway-as-a-service.html. Finally please remember that Citrix Cloud is consistently been updated and upgraded with new feature so please please refer to the online documentation and the service overview of Citrix Cloud even a day after posting the blog article as it may become out of date! You’ve been warned!
6. No support for Unified experiences (e.g Branding with your logo, colour scheme).
7. No support for Two Factor Authentication.
8. No support for authentication via outbound proxies for access outside of the resource location over the internet.
Citrix Cloud – NetScaler Gateway Service (NGS) Offering
You can find out more about the NGS subscription options which is avaiable at – https://www.citrix.com/products/citrix-cloud/subscriptions.html#tab-41499 and the service overview at – https://www.citrix.com/products/citrix-cloud/services.html#tab-23235