A question I’m often asked in the field is how do I get to the Citrix Virtual Apps and Desktops (CVAD) Service at pace or more importantly on my own terms?
The answer can be simple and complex at the same time the previously consultant in me says now says “well it depends”. The challenge with the tag line of “well it depends” often can lead to assumptions like migrating from an on-premises CVAD environment to the CVAD Service is a long and lengthy process that’s cumbersome, however today it couldn’t be further from the truth.
I have worked with many a customer that rotated to the CVAD Service in less than a month to keep either business operations continuing at a time when a crisis hit or a number of impending mergers where occurring and they needed an agile and flexible IT delivery strategy which Citrix Cloud platform is well placed to facilitate and orchestrate bringing together many different workload types in any cloud type – private, public, hybrid and most importantly hybrid multi-cloud environments.
How did these customers achieve this feat? Before I get there remember there is a lot more that needs to be consider with a traditional CVAD deployment (install, upgrade etc), requiring multiple teams to be engaged simultaneously as one (a huge feat in itself which rarely works well as a well oiled machine) from IT to InfoSec, Network and Security teams e.t.c, when you pivot to the Citrix Cloud platform you’re moving to a combination of SaaS (Gateway Service) and PaaS (CVAD Service) and equally removing a fair amount of unnecessary technical and culture debit + resistance. The lost time and productivity due to culture resistance to changing operating models and moving to the CVAD Service cannot be measured but is by far the biggest barrier in my personal field perspective.
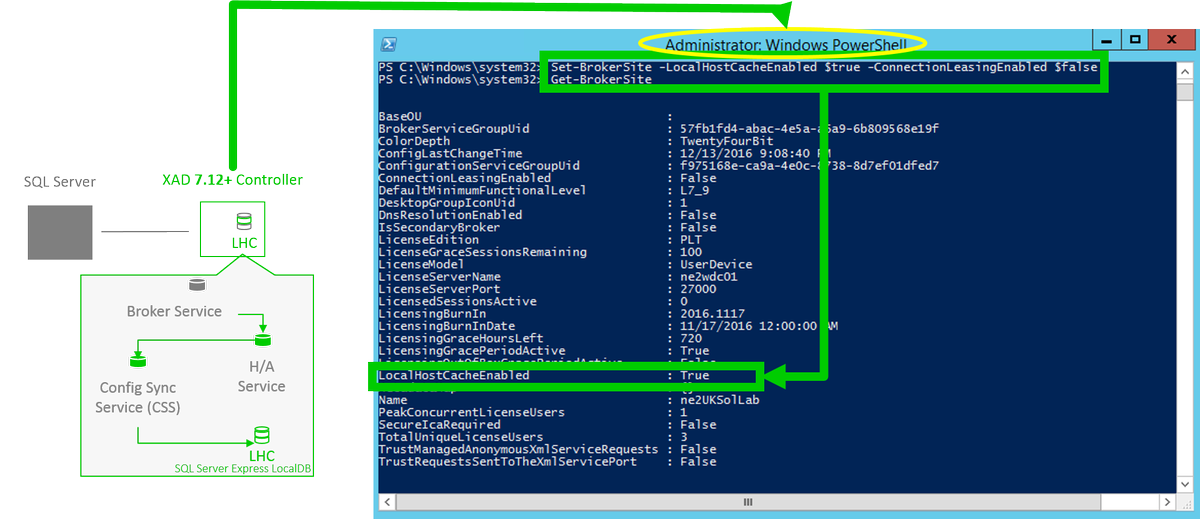
So how can you narrow the economic’s of time of getting to the CVAD Service? Citrix built and released an incredibly powerful tool called the “Automated Configuration Tool” or ACT for short, which allows for the exfiltration of your CVAD operational business logic which can be exported then evaluated and imported into your CVAD Service tenant in the Citrix Cloud by your chosen region e.g https://eu.cloud.com/. Light Bulb moment!
I previously wrote this article in http://axendatacentre.com/blog/2020/11/07/citrix-virtual-apps-desktops-or-cvad-service-migration-strategies/ – “Citrix Virtual Apps & Desktops or CVAD Service Migration Strategies” and the above and below expands upon this brief article from 2020, due to personal circumstances I stepped away largely from many communities and activities.
There are three migration strategy’s to moving to the CVAD Service from an on-premises CVAD environment:
Accelerate and Automate your Migration Strategy to @Citrix CVAD Service with less effort and friction using the Automated Configuration Tool https://t.co/rKmyOaBvRA & Site Aggregation – https://t.co/BHX55VtFf8 pic.twitter.com/5sP8besBDS
— Lyndon-Jon (L-J) Martin 👨🏻💻 📲(@lyndonjonmartin) September 30, 2021
Start A-Fresh
A complete re-evaluation of policies – employee experience vs. security, provisioning strategy. This strategy is wise if you’re well unfamiliar with new enhancements in a multi-dimensional way and been honest with that yourself your CVAD on-premises environment has not been well looked after e.g feed and watered.
Evaluate & Pivot
Migrate only key business operational IT logic requirements e.g. policies – employee experience vs. security and rebuild Machine Catalogs based upon you’re net new provisioning strategy e.g. MCS from PVS to support hybrid multi-cloud portable workloads. This strategy implies that you keep your on-premises CVAD environment feed and watered often and updated at minimum once every 12 months.
Automate & Migrate
Ingest the entire business operational IT logic from Machine Catalogs, Delivery Groups, Policies and Zones into the CVAD Service from your on-premises e.g. CVAD 1912 Long Term Service Release (LTSR) environment or preferred Current Release (CR) provided that this environment has been well looked after proactively. You will still require a brief evaluate phase during the migration as part of good leading practise and hygiene.
To get started with how-to use and get the ACT tool checkout this useful Citrix TechZone PoC guide/article – https://docs.citrix.com/en-us/tech-zone/learn/poc-guides/citrix-automated-configuration.html.
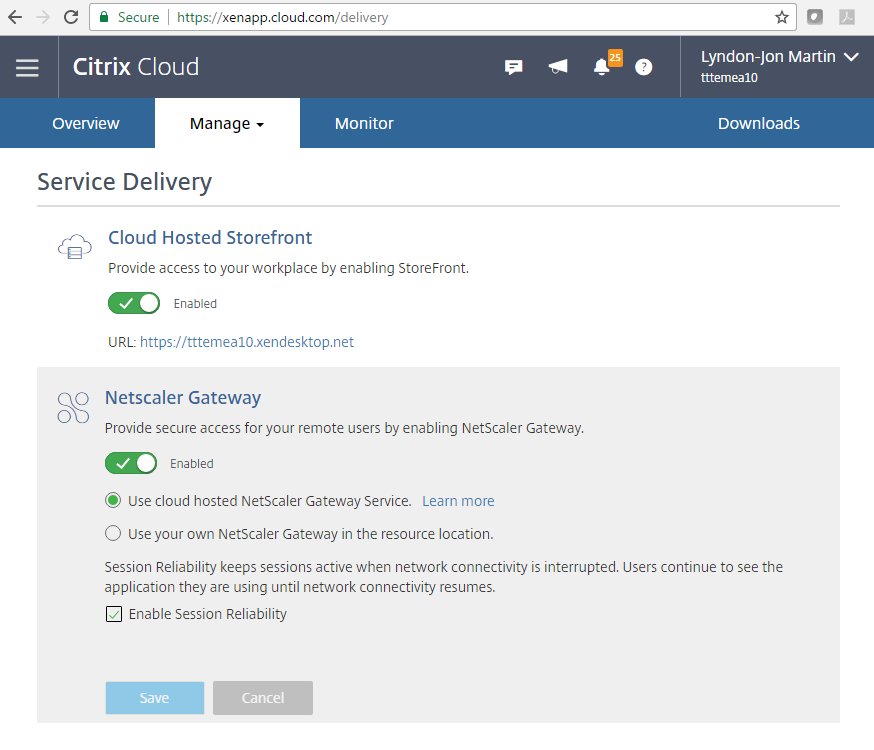
Finally the simplest and most powerful strategy is to not move any business operational IT logic at all to the CVAD Service initially but you leverage the power of “Affordance” or the appearance of providing the employee with the Citrix Workspace experience vs. StoreFront but technically nothing has changed, all that you are doing is changing the access the lens/portal to be Citrix Workspace. This strategy is fundamentally critical in enabling IT to pivot to the CVAD Service on there own terms as once the employee culture or shock has worn off with this new looking interface IT can in the background begin to use things like the ACT to migrate to the CVAD Service on there own terms and then equally shift there existing ICA proxy configurations to a turn-key SaaS operating model by unlocking the Gateway Service in the Citrix Cloud for the CVAD Service and many others Citrix Cloud Services e.g Secure Workspace Access, the Gateway Service in the Citrix Cloud platform is the default how-to access CVAD workloads, but if you still prefer an on-premises Citrix (ADC) Gateway V/A it’s a case of toggling off the Gateway Service. Customers choose to keep there Citrix ADC V/A for many different reasons and still highly relevant use cases and business or security and governance requirements.
To learn more about the “Site Aggregation” check out – https://docs.citrix.com/en-us/citrix-workspace/add-on-premises-site.html to get stated and to begin your pivot to CVAD Service on your own terms.
The views expressed here are my own and do not necessarily reflect the views of Citrix.