The views expressed here are my own and do not necessarily reflect the views of Citrix.
Category Archives: Citrix Receiver
Citrix Innovation Award Finalists for #CitrixSynergy 2018
Its that time of the year where you Citrix customers, partners can vote for your favourite Citrix Innovation Award Finalist.
This year see’s a great mixture of customers in different markets all leveraging Citrix technologies as the enabler for transformation within there organisations to embrace a new way of working or #ThisIsHowTheFutureWorks powered by Citrix Networking, Workspace and Security & Platform Analytics from https://www.cloud.com/.
I would encourage you to watch all three videos describing there journey before casting your vote as there is some really great innovation happening within these Citrix customers and if you want to get started visit https://www.citrix.com or https://www.cloud.com/ today.
Beazley from the UK – Insurance
Quote “A new mindset to work wherever I am, because I have the tools that Citrix provides and Beazley…” – @dalesteggles
Health Choice Network, US – Healthcare
WAGO, Germany – Engineering
All the very best to this years Finalists.
The views expressed here are my own and do not necessarily reflect the views of Citrix.
Citrix Ready WorkspaceHub Tech Preview (TP) Getting Started?
The following content is a brief and unofficial prerequisites guide to setup, configure and deploy the Tech Preview of the Citrix Ready WorkspaceHub using an Android Receiver on a mobile smart phone (April 2018) with XenApp & XenDesktop 7.6+ LTSR. The views, opinions, and concepts expressed are those by the author of this entry only and do not necessarily conform to industry descriptions or leading best practises. The views expressed here are my own and do not necessarily reflect the views of Citrix.
Shortened Names
SECURITY – sec
NETSCALER – ns
NETSCALER GATEWAY SERVICE – nsg service
WINDOWS – win
XENAPP – xa
XENDESKTOP – xd
XENAPP/XENDESKTOP – xad
WORKSPACEHUB – wh
Introduction
Citrix has recently announced the availability of the Tech Preview of the Citrix Ready WorkspaceHub at – https://www.citrix.com/blogs/2018/04/04/its-here-download-the-citrix-ready-workspace-hub-tech-preview-today/. So what exactly is it? Its a Raspberry Pi 3 platform at its core with Citrix technology + innovation built into it to provide a number of innovative capabilities for the Digital Workplace #thisishowthefutureworks. For me seeing is believing so the below embedded Tweet by Bas Stapelbroek – @hapster84 or https://twitter.com/hapster84 is a short video clip that demonstrates just one of the many powerful capabilities (sign-on to a thin client using a QR code while your virtual desktop still runs on your smart phone smooth roaming +++++ I like to say) available as part of the Citrix Ready Workspace Hub.
Trying out the NComputing Pi with the new Citrix Workspace Hub 😎#citrix #ncomputing with @MarkTilleman pic.twitter.com/xtiAaJfJ4T
— Bas Stapelbroek (@hapster84) April 5, 2018
Full credit of the above goes out to Bas Stapelbroek – @hapster84 and thank you for allowing me to include it in my blog post.
You’re probably asking yourself how do you manage them you ask? You leverage Stratodesk NoTouch – https://www.stratodesk.com/products/workspace-hub/ whom work with our supported Citrix Ready Partners that provide the Citrix Ready WorkspaceHub for Internal or external you can use Citrix XenMobile+.
Please visit the StratoDesk webpages for nComputing – https://www.stratodesk.com/products/workspace-hub/ncomputing-rx-hdx-citrix/ and ViewSonic – https://www.stratodesk.com/products/workspace-hub/viewsonic-sc-t25-citrix-hdx-ready-pi/ for more details around the capabilities, specifications e.t.c of each platform.
You can put the device down and lock it but be sure to refer to *page 14 for helpful tips.
Pre-requitstes & System Requirements
You’ll need to sign-up to the Tech Preview program at – https://podio.com/webforms/20685654/1419376 however I urge you to please please please read through this Citrix Forum Discussions post at – https://discussions.citrix.com/topic/394304-welcome-to-the-tech-preview-of-the-citrix-ready-workspace-hub/ and finally you should before you get started once you have your h/w and have been accepted into the program read through the the TP documentation available at – * https://docs.citrix.com/content/dam/docs/en-us/xenapp-xendesktop/current-release/downloads/workspace-hub-preview-2018.pdf which is the below in more detail.
– Your require at a bare minimum XenApp 7.6 LTSR environment running 7.6 VDA for Windows Server (remember this is a Tech Preview ONLY as of April 2018)
– You require a physical Citrix Ready WorkspaceHub device – http://citrixreadyprogram.com/workspace-hub/ which currently includes thin client vendors in alphabetical order nComputing and ViewSonic. If you have had it for a while e.g 2017 firmware please read pages 2 (end)-3(top) for instructions on where to obtain the firmware updates. See page 2 for full h/w details.
– TP only supports Android Receiver 3.13.5 or later for Mobile devices + Bluetooth for
– Networking persecutive your require Android smart phone and WorkspaceHub to be on the same Wi-Fi network with the following open ports 55555, 55556 (default port for SSL connections) and ports 1494 and 8500 must not be blocked for Citrix Casting to work between the Android Receiver on Mobile Device <-> Citrix WorkspaceHub.
– Internal centralised management utilises Stratodesk https://www.stratodesk.com/kb/Main_Page to get started or for external management you can use XenMobile+ also on page 3.
– If you’re looking for Skype for Business support check out page 5
– Recommended HDX Graphics Mode and policy for the TP is to set and enable H.264 for fullscreen the policy is “Use video codec for compression” setting to “For the entire screen”
– Setting up Receiver page 7 ensuring that you DO NOT SELECT e.g UNTICK “Add account type as Web Interface” and during the setup you’ve need to complete the Touch-Free mode for proximity authentication enabled vs. disabled page 8-9. Now test the proximity referring to page 10.
– Setting up the session roaming with a QR code, TLS/SSL (requires SHA256is covered in pages 11-15 with Stratodesk NoTouch
– Please please please read through thoroughly the known limitations within the TP on page 16 and finally there is Citrix Discussions Forum available for support during the TP at https://discussions.citrix.com/forum/1726-citrix-ready-workspace-hub-preview/.
In Closing
I hope you found this blog post useful as I have written it due to the number of people contacting me via social platforms, Slack and of course traditional communications like telephone calls, text/sms and yes email. A final thought, be sure to check out a short demonstration + talk on Citrix Casting and a lot more detail at – https://www.citrix.com/products/citrix-workspace/iot.html.
Disclaimer
Please read the “Citrix Ready Workspace Hub PreviewDisclaimerCitrix Ready Workspace Hub Preview Citrix Ready Workspace Hub Preview” on page 1* and a note to Citrix Investors is listed at the bottom of the blog post announcement of the TP program of the Citrix Ready WorkspaceHub at – https://www.citrix.com/blogs/2018/04/04/its-here-download-the-citrix-ready-workspace-hub-tech-preview-today/.
Session Watermarking for App & Desktop Security by Citrix XenApp & XenDesktop 7.17 or #CitrixCloud
The following content is a brief and unofficial prerequisites guide to setup, configure and deploy Session Watermark policy feature with the XenApp & XenDesktop Service (April 2018) or XenApp & XenDesktop 7.17 on-premises prior to deploying in a PoC, Pilot or Production environment by the author of this entry. The views, opinions and concepts expressed are those by the author of this entry only and do not necessarily conform to industry descriptions or leading best practises. The views expressed here are my own and do not necessarily reflect the views of Citrix.
Shortened Names
SECURITY – sec
NETSCALER – ns
NETSCALER GATEWAY SERVICE – nsg service
WINDOWS – win
XENAPP – xa
XENDESKTOP – xd
XENAPP/XENDESKTOP – xad
Introduction to “Session Watermark”
The latest release of the XenApp & XenDesktop Service powered by Citrix Cloud or if you are performing a private cloud (on-premises) upgrade or net new installation of XenApp & XenDesktop 7.17 has some NEW features (another post brewing) and one that I have been waiting on for quiet sometime now has not finally arrived (WAHOO!) and its VERY VERY simple to configure and aids in improving your security posture (I believe) for delivery of apps & desktops powered by Citrix against e.g IP theft. In the below tweet can you see it?
App & Desktop #Security made simple with #Citrix @XenApp & @XenDesktop Service powered by @CitrixCloud although my #ISP needs nudge once again!!!!! pic.twitter.com/fKAPXxNiT8
— Lyndon-Jon Martin (@lyndonjonmartin) April 3, 2018
The above is from my initial tests using a Windows Server 2016 VM hosted in Azure Northern Europe region running the 7.17 VDA configured to my Citrite #CitrixCloud XenApp & XenDesktop Service so I did not need to upgrade anything to get this new SHINY cool feature yes I said it SHINY. All I was required to do was deploy a new Windows Server 2016 VM from the Azure marketplace, domain join it, install the VDA and connect it to my Cloud Connector and I was ready in less than 25 minutes from initially deploying the VM from the marketplace.
Finally on a personal note for me Citrix SysAdmins enabling the “Session Watermark” feature obviously initally tested in a safe environment e.g UAT with a few users from a couple of departments and then rolling it out into production (as when/how your ready) will be making IT the modern “App & Desktop Security Heroes“. IT can apply and configure these new policies to be the most right vs. relevant for your organisations security needs while not hindering the end-users Rich HD eXperience.
Session Watermark Policies
You have 8 watermarking policies to apply with the 9th one enabling this security capability or feature set with the following list of quirks, suggested policy configuration and more available at – https://docs.citrix.com/en-us/xenapp-and-xendesktop/current-release/policies/reference/ica-policy-settings/session-watermark-policy-setting.html.
Before we get started it is worth mentioning that this feature does add an overhead to the compute on the backend (VDA side) and therefore it is suggested to enable up to two water marking features or items. In my overview of this feature I will wont cover off the cost of implementing this security policy as there are multiple variables to consider e.g HDX Graphics Mode and associated policies to provide the right vs. relevant end-user experience vs. how many watermark items do I apply? I have begun testing so bare with me and I’ll publish my findings either on my personal blog here or on https://www.mycugc.org under the “Expert Insights” area.
“Enable session watermark”
By default this feature is DISABLED as the default behaviour which I believe is the right approach considering its Citrix’s initial release of this #security feature (in my personal view) and secondly online documentation at eDocs suggested recommendations it to enable NOT more than two watermark text items. Finally * indicates that this policy is DISABLED by default when Session Watermark is enabled.
Include client IP address
* This is the IP addr of the device connecting to the virtual app & desktop.
Include connection time
* Utilises the following format yyyy/mm/dd hh:mm to display the users initial connection time to there virtual app or desktop.
Include logon user name
ENABLED by default when you enable Session Watermark as a policy and uses the following format USERNAME@DOMAINNAME is most optimise for 20 characters or less otherwise truncation might occur of the users logon username.
Include VDA host name
ENABLED by default when you enable Session Watermark as a policy and provides the VDA hostname e.g ne1vad01
Include VDA IP address
* Provides the internal IP addr that corresponding the VDA’s hostname e.g ne1vad01 = 10.1.0.7
Session watermark style
ENABLED by default using “Multiple e.g displays five watermark labels” when you enable Session Watermark as a policy or you can configure “Single e.g displays a single watermark label in the centre of the session“. TIP switching to SINGLE and sticking to two watermark text items for me in my initial tests is a good starting policy however time will tell as I continue to test out this new feature and its capabilities with different HDX Graphics Modes and associated tweaks.
Watermark custom text
* A unicode maximum of 25 characters is supported if you exceed this limit it will be truncated.
Watermark transparency
ENABLED by default set to “17 out of 100” when you enable Session Watermark as a policy, personally I think setting it to just 1 is fine in my initial tests as you want it to be not so in your face to the end-users to be bluntly honest.
Understanding What’s New with the latest XenApp & XenDesktop 7.15 LTSR
The following content is a brief and unofficial prerequisites guide to setup, configure and test accessing secure by design virtual apps and desktops powered by XenApp & XenDesktop 7.15 prior to deploying a PoC, Pilot or Production environment by the author of this entry. The views, opinions and concepts expressed are those by the author of this entry only and do not necessarily conform to industry descriptions or leading best practises. The views expressed here are my own and do not necessarily reflect the views of Citrix.
Shortened Names
WEB INTERFACE – wif
LONG TERM SERVICE RELEASE – ltsr
CURRENT RELEASE – cr
FEDERATED AUTHENTICATION SERVICE – fas
SECURITY ASSERTION MARKUP LANGUAGE – saml
IDENTITY PROVIDER – idp
NETSCALER UNIFIED GATEWAY – nug
XENAPP – xa
PROVISIONING SERVICES – pvs
XENDESKTOP – xd
XENAPP/XENDESKTOP – xad
STOREFRONT – sf
What is the difference between LTSR vs. CR for XenApp & XenDesktop 7.x?
The Long Term Service Release (LTSR) program for XenApp and XenDesktop provides stability and long-term support for XenApp/XenDesktop releases while the Current Release (CR) provides customers with the very latest version of XenApp and XenDesktop which includes the latest innovations e.g EDT v2
XenApp & XenDesktop 7.15 LTSR Feature Summary Comparison with 7.6 LTSR
The following is a simple one PDF page document that lists all the feature capabilities from initial first LTSR which was XenApp & XenDesktop 7.6 Feature Pack (FP) 1-3 through to the current LTSR XAD 7.15 including the CR releases in-between so its absolutely worth booking marking in your browser or better yet download it to keep it to hand for customer conversations – https://www.citrix.com/content/dam/citrix/en_us/documents/data-sheet/xenapp-xendesktop-715-ltsr-feature-summary-comparison-to-76-ltsr.pdf.
Noteworthy Points What’s New vs. Excluded
I’d very strongly recommend that your read the following CTX article – https://support.citrix.com/article/CTX205549 entitled “CTX205549 FAQ: XenApp, XenDesktop, and XenServer Servicing Options (LTSR)” and to ensure that you remain compliant post your update/migration to 7.15 LSTR you should download the “CTX209577 Citrix LTSR Assistant” https://support.citrix.com/article/CTX209577
Its also worth noting the following that are classed as “Excluded Features/Components/OSes” from the XAD 7.15 LTSR but I’d like to stress PLEASE PLEASE refer for eDocs for full caveats vs. supporting statements at – https://docs.citrix.com/en-us/xenapp-and-xendesktop/7-15-ltsr/whats-new/7-15-ltsr-initial-release-.html+ and these listed notes are based upon the initial release however there is now a Cumulative Update 1 (CU1) already available so be sure to read through it as well at – https://docs.citrix.com/en-us/xenapp-and-xendesktop/7-15-ltsr/whats-new/cumulative-update-1.html.
OSes+
– Windows 2008 32-bit (for Universal Print Server)
Behavioural Changes
– Upgrading a XA 6.5 worker to a new 7.15 VDA is now slightly different and the detailed process is listed at – https://docs.citrix.com/en-us/xenapp-and-xendesktop/7-15-ltsr/upgrade-migrate/upgrade/upgrade-xenapp-6-5-to-vda.html and also be sure to review the XenApp 6.x Migration Tool at – https://docs.citrix.com/en-us/xenapp-and-xendesktop/7-15-ltsr/upgrade-migrate/xenapp-worker-upgrade.html and you review the migration tool by watching the embedded YouTube video below.
Finally while your planning your migration to XA 7.15 (FMA) from 6.5 (IMA) you will mostly likely be upgrading vs. migrating away from WIF so please be sure to read and how to migrate features to StoreFront from your WIF environment at – https://docs.citrix.com/en-us/storefront/3-12/migrate-wi-to-storefront.html. Equally I’d encourage any organisation reading this to review how-to setup and configure the “unified user experience” for Citrix Receiver vs. the Green Bubbles which will provide a much better experience for users you can enable it by quiet easily once you’ve read through the following article in eDocs at – https://docs.citrix.com/en-us/storefront/3-12/manage-citrix-receiver-for-web-site/unified-receiver-experience.html.
– Follow the supported leading best practises for upgrading the 7.15 LTSR by reviewing the following node within Citrix’s eDocs – https://docs.citrix.com/en-us/xenapp-and-xendesktop/7-15-ltsr/upgrade-migrate/upgrade.html
– VDA installation failures for Win 10 N Editions that don’t include Microsoft Media Foundation can now be acknowledged via the installation GUI of the VDA vs. automated deployed (unattended) there is a new option “/no_mediafoundation_ack“.
Excluded Features & Compoments+
– HDX Graphics Mode – Framehawk
– StoreFront Citrix Online Integration
– AppDisks
– Personal vDisk is excl for Win 7, 10
– Load balancing of Session Recording which was an experimental feature in 7.14
What’s Deprecated in the 7.15 LSTR
A full list of what is deprecated is available at – https://docs.citrix.com/en-us/xenapp-and-xendesktop/7-15-ltsr/whats-new/removed-features.html and I am only going to list a few points that I believe of most interest to those whom read my blogs or if your just a Citrix SysAdmin vs. Consultant reading this blog post.
– No VDA installations on Windows XP will be supported
– Flash Redirection ++Hello HTML5 GOODBYE Flash wahoo!
– Citrix Receiver for Web classic experience (“green bubbles” user interface) ++Oh YES double wahoo!
– VDAs on Desktop – Windows 10 version 1511 & Windows 7, 8.1 and for Server – Windows Server 2008 R2 and Windows Server 2012
– Legacy Thinwire + DirectX Command Remoting (DCR) switch to Thinwire ECM or Adaptive Display v2 see – https://docs.citrix.com/en-us/xenapp-and-xendesktop/7-15-ltsr/graphics/thinwire.html
– In-place upgrades of certain XAD infrastructure components aren’t supported!
– Studio on Windows 7
– Azure Classic support
++ Personal comment vs. note from the author of the post
XenApp and XenDesktop 7.15 LTSR baseline components
VDA for Desktop OS 7.15
VDA for Server OS 7.15
Delivery Controller 7.15
Citrix Studio 7.15
Citrix Director 7.15
Group Policy Management Experience 3.12
StoreFront 3.12
Provisioning Services (PVS) 7.15
Universal Print Server 7.15
Session Recording 7.15 (Platinum Edition only)
Linux VDA 7.15 (See the Linux VDA documentation for supported platforms)
Profile Management 7.15
Federated Authentication Service 7.15
7.15 LTSR Compatible Components and Platforms
AppDNA 7.15
Citrix SCOM Management Pack for License Server 1.2
Citrix SCOM Management Pack for Provisioning Services 1.19
Citrix SCOM Management Pack for StoreFront 1.12
Citrix SCOM Management Pack for XenApp and XenDesktop 3.13
HDX RealTime Optimization Pack 2.3
License Server 11.14.0 Build 21103
Workspace Environment Management 4.4
App Layering 4.3
Self-Service Password Reset 1.1
What’s New
– Machine Catalog’s functional level within your Site from 7.9 do not require an upgrade
– Machine Creation Services (MSC) now supports generation 2 VMs with Microsoft System Center Virtual Machine Manager SCVMM
– The FMA or 7.x version of Local Host Cache (LHC) is now enabled by default BUT note that if it was disabled from a prior release of the XAD 7.x then you need to enable it and disable Connection Leasing (CL) https://docs.citrix.com/en-us/xenapp-and-xendesktop/7-9/manage-deployment/connection-leasing.html which was initially introduced into the 7.x platform to provide a fallback if your SQL database connection was lost or unavailable until LHC was re-introduced in XAD 7.12 – https://docs.citrix.com/en-us/xenapp-and-xendesktop/7-12/manage-deployment/local-host-cache.html but was not enabled by default in the 7.12 release CL was primarily utilised.
– Director App Failure Monitoring – https://docs.citrix.com/en-us/xenapp-and-xendesktop/7-15-ltsr/policies/reference/virtual-delivery-agent-policy-settings/monitoring-policy-settings.html#App_Failure_Policy_Settings
Security Leading Best Practises
– General Overview https://docs.citrix.com/en-us/xenapp-and-xendesktop/7-15-ltsr/secure/best-practices.html.
– Securing your StoreFront 3.12 environment – https://docs.citrix.com/en-us/storefront/3-12/secure.html
– Standardise on a single organisation user identity platform e.g AAD by leveraging NetScaler + + StoreFront + FAS which can convert SAML vs. OAuth tokens into virtual smartcards per configured Store within StoreFront to then SSO a user onto there intended virtual apps & desktops without requiring to re-enter his/her in a directory username + password for that resource location (What’s this? Read – https://docs.citrix.com/en-us/citrix-cloud/citrix-cloud-resource-locations.html).
– Slightly obvious to an Citrix expert vs. Citrix Partner but its worth highlighting for newbies to Citrix virtualisation technologies is that XAD management provides Delegated Administration to manage just enough access for different members of the IT vs. compliance departments/business units to have just enough access to complete there daily vs. weekly vs. monthly activities vs. tasks – https://docs.citrix.com/en-us/xenapp-and-xendesktop/7-15-ltsr/secure/delegated-administration.html and for remote secure access to virtual apps & desktops you will need implement NetScaler Unified Gateway – https://docs.citrix.com/en-us/xenapp-and-xendesktop/7-15-ltsr/secure/storefront-netscaler.html which can also enable and allow your organisation to control authentication at the edge of your network e.g 2FA vs. MFA vs. using Biometrics with supported 3rd Citrix Ready solutions so check out – https://citrixready.citrix.com. Finally you can also engage with SmartAccess capabilties when fronting XAD for R/A with NUG so check out the following resources for NS 11.x.n – https://docs.citrix.com/en-us/netscaler-gateway/11/integrate-web-interface-apps/ng-smartaccess-wrapper-con/ng-smartaccess-xd-config-con.html and NS 12.x.n – https://docs.citrix.com/en-us/netscaler-gateway/12/integrate-web-interface-apps/ng-smartaccess-wrapper-con/ng-smartaccess-xd-config-con.html and there is also a CTX article entitled “CTX227055 Smart Access Guide for NetScaler Gateway, StoreFront and XenDesktop” to review at – https://support.citrix.com/article/CTX227055 and finally you can configure Pre-Authentication scans to check that the connecting end-point is compliant (Refer to VDI Handbook section below).
– Enabling TLS or Transport Layer Security for ICA/HDX Session – https://docs.citrix.com/en-us/xenapp-and-xendesktop/7-15-ltsr/secure/tls.html for a detailed how-to from the first LTSR check out the following blog article at – https://www.citrix.com/blogs/2014/12/11/how-to-secure-ica-connections-in-xenapp-and-xendesktop-7-6-using-ssl/ or download the white paper entitled “Citrix XenApp and XenDesktop 7.6 LTSR FIPS 140-2 Sample Deployments” from – https://www.citrix.com/content/dam/citrix/en_us/documents/about/citrix-xenapp-and-xendesktop-76-fips-140-2-sample-deployments.pdf. During some research I also came across the following CTX article to disable TLS 1.0 for XAD 7.6 LTSR which may or may not be useful to you check out – https://support.citrix.com/article/CTX215447.
– How do I assign the right vs. relevant security or UX policy? Refer to the built-in policy templates which you can read at – https://docs.citrix.com/en-us/xenapp-and-xendesktop/7-15-ltsr/policies/policies-templates.html which include the same policy type for modern vs. legacy OSes.
Citrix VDI Handbook for the 7.15 LTSR
Recommended pages of interest to read from “Citrix VDI Best Practices for XenApp and XenDesktop 7.15 LTSR” – https://docs.citrix.com/content/dam/docs/en-us/xenapp-xendesktop/7-15-ltsr/downloads/Citrix%20VDI%20Handbook%207.15%20LTSR.pdf which I am commonly asked about so I thought it makes sense with the current LTSR to list them out here for everyone to focus on what is right vs. relevant for PoC’s e.t.c
– Page 11 which focus on CCS Methodology
– Page 32 Five-Layer Design Model and Conceptual Architectures for XAD environments
– Page 35-37 Site topology covering latency, bandwidth vs. number of users
– Page 50-52 covers StoreFront keywords to the behaviour of the delivery of virtual resoucres
– Page 52 Scaling vs. sizing of your StoreFront cluster
– Page 54 Calculate what NetScaler required SSL through-put however i’d strong recommended engage with your Citrix rep for leading best practise vs. guidance as this can/may differ dependant upon your choose appliance vs. firmware version.
– Page 58 Implement GSLB with HDX Optimised routing to ensure connecting users in a regional vs. global deployment connect to better NUG by proximity.
– Page 63 HDX Display Protocol
– Page 66- User Profile types for Local, Roaming, Mandatory & Hybrid vs. virtual apps & desktop chooses model
– Page 79 Built-in Policy templates to optimise the UX based upon your organisational requirements
– Page 88-93 vCPU/RAM/Storage I/O vs. User workload types light, medium and heavy
– Page 94-97 SQL database sizing vs. scaling 5K up to 15K including expected database growth
– Page 98-99 PVS SQL database guidance for suggested sizing
– Page 104 XAD Controller sizing vs. scaling per 5K users which also includes a calculation
– Page 105 LHC considerations if enabled to re-size your control infrastructure for XAD
– Page 107 Citrix Cloud connector sizing for 5K users in private vs. public cloud
– Page 113-116 SQL Database sizing
– Page 121-129 PVS Accelerator with XenServer
– Page 132-140 Hardware Formulas for sizing vs. scaling including GPU(s)
Deploying a XAD 7.15 LSTR PoC
Coming…
What Citrix Receiver & HDX Optimisation Pack should I deploy?
You should consider reviewing and if fit for purpose for your organisation implement the Windows 4.9 LTSR Citrix Receiver version – https://docs.citrix.com/en-us/receiver/windows/4-9.html along with if you utilise Skype for Business for UC the LTSR of the HDX Optimisations Pack – https://docs.citrix.com/en-us/hdx-optimization/2-4-ltsr.html and you can find out more information about the lifecycle at – https://support.citrix.com/article/CTX200466.
My Best of #CitrixSynergy 2017
The views expressed here are my own and do not necessarily reflect the views of Citrix.
Shortened Names
CITRIX USER GROUP COMMUNITY – cugc
HYPER CONVERGED INFRASTRUCTURE – hci
Introduction
Its my 5th #CitrixSynergy and this is def one of the best Synergy’s I have ever had the privilege of watching virtually from London, England. Why not in person? I prefer to watch virtually as I am to consume more content faster and translate that into content to update Citrix partners/customers in a timely manner at high level and tech deep dive where required in particular areas or topics. Finally this blog post will most likely change over the next 2-3 weeks as I consume all of the Synergy 2017 content as when/how I can.
My Highlights of the Key Notes
Vision Keynote
– 4:45 Citrix User Group Community – https://www.mycugc.org THANK YOU! Join the community today its powered by some of the most passionate Citrix and Technology advocates from around the global!
– 11:00 Red Bull Racing I’m not going to say anything you need to watch it!
– 21:45 Cloud powers the world
– 27:00 Digital Frontier Companies
– 39:00 Citrix Secure Digital Workspace with a software-defined preimeter
– 40:57 Citrix Workspace Services and a brief demonstration by Citrix’s CEO
– 42:25 SD-WAN / Gateway / WebApp Firewall / DDoS (NS 12+) as a Service
– 47:35 Citrix Analytics Service
– 1:01:00 “Better Together” and video message from Microsoft CEO Satya Nadella
– 1:12:25 Citrix + Google Chromebook (Skype for Business, Office365 and much more…)
– 1:18:00 Healthcare customer story “Partners Healthcare”
Technology Keynote
– 22:00 Unified Workspace (its Adaptive and Contextual by device/location and it changes the users published resources and its access type!) which brings together some of the most crucial aspects of todays modern apps, desktops, data & your location in a single view with casting capabilities but not demoed as instead instead*
– 29:00 *Workspace IoT (SmartSpaces) demonstration with a users own mobile phone enables an auto login to a Win 10 VD at guest location including welcoming the user based upon his/her smart phone used as there identity. Security people feel free or you will be going nuts right now!
– 32:30 Its all about layering you guessed it Citrix App Layer enabling IT to say YES! Note demo was demoed using a Samsung DEX check it out – https://www.citrix.com/blogs/2017/03/29/instant-desktop-computing-from-the-new-samsung-galaxy-s8-smartphone/
– 39:40 Workspace Appliance Program e.g HCI
– 42:35 Protect against Zero day attacks with XenServer and BitDefender which is available but is something which Citrix announced on 21/06/2016 yes thats right 2016 entitled “A Revolutionary Approach to Advanced Malware Protection” – https://www.citrix.com/blogs/2016/06/21/a-revolutionary-approach-to-advanced-malware-protection/ 21/06/2016 yes 2016!
– 47:00 Brad Anderson Corporate Vice President of the Enterprise Client & Mobility @Microsoft discusses shortly and then prefers to demonstrates our joint Citrix + Microsoft “Better Together” capabilities in Mobility, Virtualisation delivery from Azure and more.
– 1:01:38 Digital Jungle discussion its def worth your time if you about security and managing the experiences of your users workspace!
– 1:47:25 Vision of how the Digital Workspace is going to evolve
Citrix Synergy TV Breakout Sessions
The following are my current top sessions to watch in no particular order that I believe you’ll gain a lot of value out of watching BUT note that this may change as I continue to consume more of the on-demand content from Synergy 2017.
– SYN318 A to Z: best practices for delivering XenApp, XenDesktop – https://www.youtube.com/watch?v=jnnZTKBy18c&feature=youtu.be
– SYN111 – What’s new with Citrix Cloud and what’s to come – https://www.youtube.com/watch?v=C-UunHGKqLY
– SYN120 – NetScaler SD-WAN updates – https://www.youtube.com/watch?v=CdqIkCb86uU
– SYN103 – Citrix App Layering – https://www.youtube.com/watch?v=KBYoVeAYnSA
– SYN118 – What’s new with NetScaler ADC – https://www.youtube.com/watch?v=uMefjGwRMeU
– SYN121 – What’s new with NetScaler Unified Gateway – https://www.youtube.com/watch?v=-ovb4TIb5JY&t=28s
– SYN115 – Why should I use ShareFile if I already have Office 365? – https://www.youtube.com/watch?v=kESgKT7_mJw
Innovation Super Session
Awaiting for the on-demand video publication but for now I will leave you with the following Tweet as a thought or rather a reminder to make sure that you watch it if you missed it!
A standing ovation for Gen. Colin Powell as he takes the stage at #CitrixSynergy pic.twitter.com/VtH86wAvFL
— Citrix (@citrix) May 25, 2017
Synergy 2017 Advocates Blog Posts
Citrix Synergy 2017 – It’s a Wrap – See all the most important announcements listed here! By Christiaan Brinkhoff. – https://blog.infrashare.net/2017/05/29/citrix-synergy-2017-its-a-wrap-see-all-the-most-important-announcements-listed-here/
XenApp Essentials Services Understood powered by Citrix Cloud
The following content is a brief and unofficial prerequisites guide to setup, configure and test delivering virtual apps from the Microsoft Azure Marketplace powered by the Citrix Cloud XenApp Essentials Service prior to deploying in a PoC, Pilot or Production environment by the author of this entry. The views, opinions and concepts expressed are those by the author of this entry only and do not necessarily conform to industry descriptions or best practises. The views expressed here are my own and do not necessarily reflect the views of Citrix.
Shortened Names
XENAPP – xa
XENDESKTOP – xd
XENAPP/XENDESKTOP – xad
MACHINE CREATION SERVICES – mcs
AZURE REMOTEAPP – ara
XENAPP ESSENTIALS SERVICE – xes
HIGH DEFINITION EXPERIENCE – hdx
REMOTE DESKTOP SERVICES – rds
What is it?
It is a replacement for the deprecated Microsoft Azure RemoteApp (ARA) – https://blogs.technet.microsoft.com/enterprisemobility/2016/08/12/application-remoting-and-the-cloud/ (“…Support existing Azure RemoteApp customers on the service through August 31st, 2017..“) which provides simplicitic beauty of Microsoft Azure RemoteApp now with the “Secure by Design” enterprise security methodology, platform scalability with FMA in 7.x and HDX virtual app delivery protocol capabilities & power of Citrix XenApp.
ARA brought Remote Desktop Services (RDS) capabiltiies from a multi private cloud deployments on Windows Server to Azure with non-persistent RDS/RDP sessions delivered from the Microsoft Azure Cloud only! The XA Essentials Service is only available from Microsoft Azure Marketplace hosted on Azure and only supports the delivery of Windows apps delivery from Windows Server 2012 R2, 2016 prepared Templates or Bring Your Own Templates (BYOT) uploaded. Citrix has prepared a full FAQ available at – https://www.citrix.com/global-partners/microsoft/resources/xenapp-essentials-faq.html
Overviews & Demonstrations
Introducing XenApp Essentials Service is a demonstration of the Service by Citrix.
Extend the Microsoft RDS platform in Azure through Citrix solutions was a presentation at Microsoft Ignite 2016.
What Feature’s Are Available?
The following feature matrix compares XenApp, XenDesktop Platinum vs. XenApp & XenDesktop Service vs. Azure Marketplace XenApp Essentials vs. Azure Marketplace XenDesktop Essentials –
https://www.citrix.com/content/dam/citrix/en_us/documents/reference-material/xa-xd-deployment-options-feat-comp-matrix.pdf.
High Level Getting Started, System Requirements & Pre-requistes
1. You’ll need an Azure subscription with a resource group defined with a virtual network.
2. Define your preferred Azure region which you can ref from – https://azure.microsoft.com/en-gb/regions/.
3. Decide on your AD stratergy which can be Active Directory sat in the Azure resource location using a min A3 Standard VM instance for AD or you can utilise “Azure Active Directory Domain Services” and eDocs suggested that you review – https://docs.microsoft.com/en-us/azure/active-directory-domain-services/#main prior to implementing AAD for the XA Essentials Services vs. traditional AD.
4. Define your preferred OS strategy for the service which currently supports server OSes for Windows Server 2012 R2 or 2016 and you’ll need to define master image stratergy e.g BYO image or a Citrix prepared image for the service! Notes: “(a)BYO with your own Server OS template including apps + licenses for those apps or choose Citrix prepared templates with Apps. (b)RDS CALS w/SA to Azure or purchase RDS SALs.”
5. Customer owned Azure Subscription as is responsible for per monthly IaaS consumption costs e.g compute, network, bandwidth & storage
6. Only MCS based provisioning is support for public (Iaas) clouds and for this Service hosted by Microsoft Azure.
7. Subscribe to XenApp Essentials Service through Azure Marketplace at – https://azuremarketplace.microsoft.com/en-us/marketplace/apps/Citrix.XenAppEssentials?tab=Overview.
8. Connect your Azure subscription to Control Plane operated by Citrix Cloud. Citrix Cloud controls customer Azure subscription via Citrix Cloud Connectors to provide capabilities to manage, provision and monitor your XenApp servers which will deliver your HDX virtual apps
Deploying your Virtual Apps (Draft!!!)
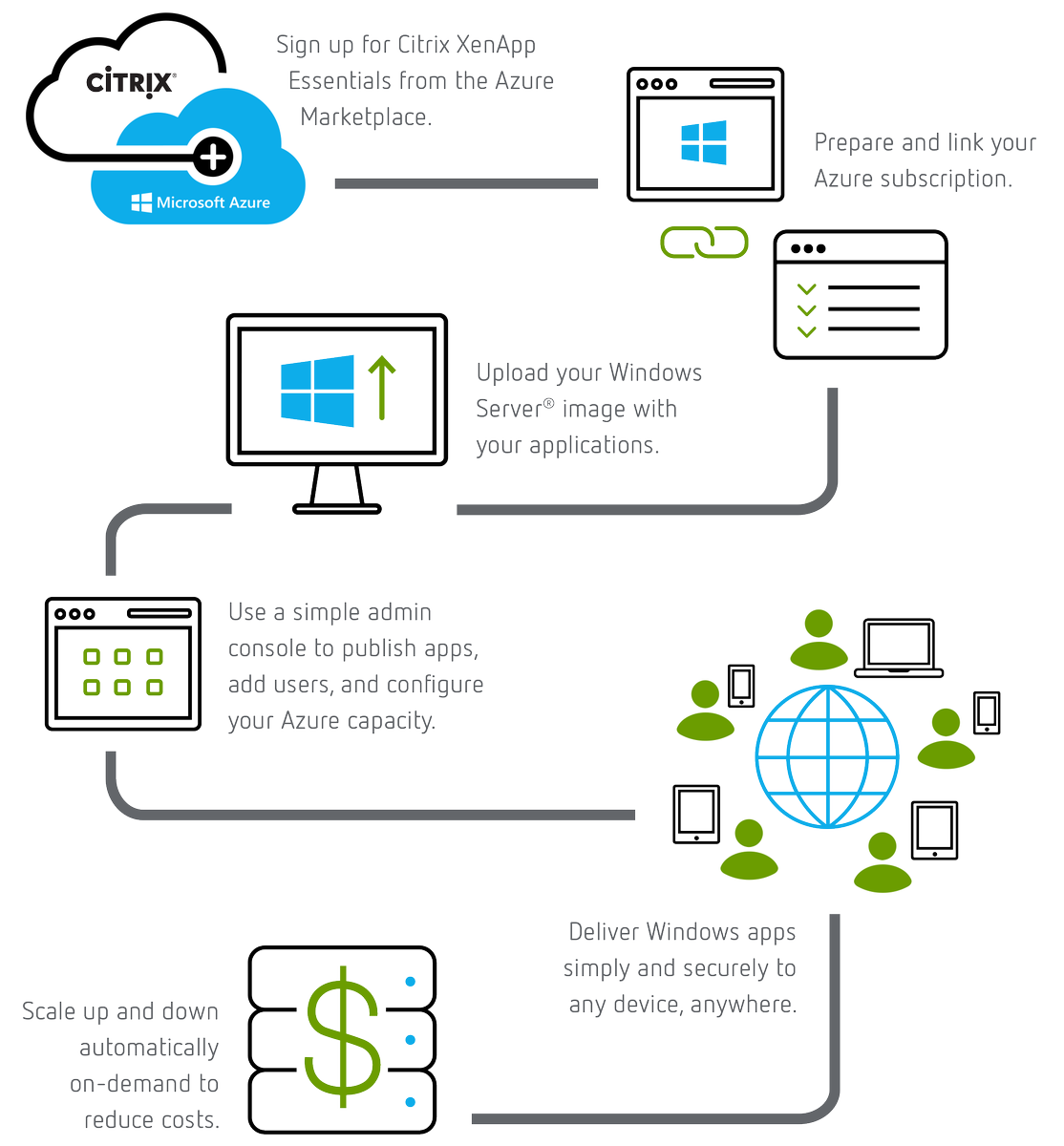
The above is an graphic from the official XA Essentials Service documentation from Citrix eDocs at – http://docs.citrix.com/en-us/citrix-cloud/xenapp-and-xendesktop-service/xenapp-essentials.html and the below is my personal text based step by step summary explaining how to get started with the XA Essential Service powered by Citrix Cloud and Microsoft Azure based upon the Ignite session at – https://www.youtube.com/embed/Ck0mtVXqOuM. Please note that these steps can change as the service is delivered from Citrix Cloud which is a secure SaaS style evergreen control plane – http://docs.citrix.com/en-us/citrix-cloud/overview/about.html.
1. Before you begin you will requires a subscription to XenApp Essentials Service from
2. Azure Marketplace + Server Images + RDS CALS w/SA
3. Create app collection similar to ARA
4. Create a name
5. Domain Joined (Popular) or Non-Domain Joined (TBC)
6. Link Azure subscription to XAE and select Resource Group, Virtual Networks & Subnet
7. Enter in Domain details which include Domain name, OU, Srv acct + passed
8. Select template image Citrix provided or your OWN
9. Select capacity and mange costs by selecting instance type and power settings scheme (saver logoff after 10min; standard after 1hr; performance after 4hrs or always on i.e do not perform any power mgmt
10. Enter in # of users concurrent and you’ll receive an estimate cost calculator prior to provisioning to understand the costs based on 40hr usage per month
Summary and the deploy
11. Time access is short as CC will provision your instances in your subscription
12. Select app collection click Apps tab then select apps to publish
13. Select users tab and search domain by user or group
14. Return to Manage home and you’ll see that your app collection is now ready with a green tick
15. Select app collection and you’ll see the StoreFront URL to send to users
16. Users login with domain\user + passed
17. Users are now able to launch there HDX virtual apps secured by there organisations Cloud-hosted StoreFront FQDN which provides secure remote access via the NetScaler Gateway Service also review caveats re bandwidth through-puts below.
Caveats, Current Known Issues with the Service
The list of current know issues one are my ones to pay attention to most as of 04/04/2017 and a full list is available at http://docs.citrix.com/en-us/citrix-cloud/xenapp-and-xendesktop-service/xenapp-essentials.html so please check and read them all!
1. Live.com accounts cannot be used for authenticaiton
2. Users cannot launch and app if an existing RDS session is present on the XA VDA worker.
3. Machine catalogue failures may occur if deploying a VM instance size in a region that does not support that instance type any more.
4. A premium storage account is not supported see “Prepare Your Azure Subscription”
5. Each end-user is limited to 1-GB outbound data transfer per month but you can increase the limit via by acquiring a 25 GB add-on via the Azure Marketplace see “StoreFront and NetScaler Gateway in XenApp Essentials Service”
6. See eDocs for more…
My New Secure Workspace Ready in less than 15 min the #CitrixLife
The views expressed here are my own and do not necessarily reflect the views of Citrix.
Overview
Today I received my new Mac, yes I’ve decided to move from a PC to a Mac for various reasons (those whom know me are probably going really!?) but I still have a Windows 10 tablet PC which I use regually at home, but most importantly my Windows 10 Citrix issued virtual desktop powered by XenDesktop (Citrix on Citrix) follows me anywhere with Citrix Receiver or the HTML5 Citrix Receiver!
I didn’t even turn on my old PC I just started working within less than 15 min from my new MacBook connected to my Win10 VD via Receiver and i’ll just sort out what I need locally like Reflector, NAMP e.t.c over the weekend as its a busy week post our local partner event Citrix Partner Accelerator.
What Did I Do?
1. Unboxed my new Macbook
2. Plugged in the power and pushed the power button its been a while since I’ve heard that CHIME 🙂
3. Completed Apples on-boarding process including setting up iCloud including connecting to the Citrix employee Wi-Fi from our London, Paddington offices check it out at – https://twitter.com/CitrixUK/status/834742107055259650
4. Next I opened Safari and navigated to http://receiver.citrix.com and it auto detected for me that I am connecting from a Mac and presented me with a download link to Receiver for Mac 12.4.
5. Once downloaded I installed it simple!
6. Opened Citrix Receiver and i entered in my addr which then prompted me for my Citrix employee username, passwd and 2FA Token
7. BOOM Receiver synced all my virtual apps & desktops that I had previously selected on other device(s) within a few moments of signing in
8. I clicked on my Windows 10 Virtual Desktop powered by XenDesktop and my new mobile #SecureWorkspace is ready to go within less than 15 minutes!
My new device & new #Citrix #SecureWorkspace unboxed, setup with #Receiver installed in less than 15 min connected to #Win10 @XenDesktop pic.twitter.com/Tv3ejuN5JZ
— Lyndon-Jon Martin (@lyndonjonmartin) March 1, 2017
What’s New in XenApp & XenDesktop 7.13
The following content is a brief and unofficial prerequisites guide to setup, configure and test delivering virtual apps and desktops powered by XenApp & XenDesktop 7.13 prior to deploying in a PoC, Pilot or Production environment by the author of this entry. The views, opinions and concepts expressed are those by the author of this entry only and do not necessarily conform to industry descriptions or best practises. The views expressed here are my own and do not necessarily reflect the views of Citrix.
Shortened Names
SECURITY ASSERTION MARKUP LANGUAGE – saml
LOCAL HOST CACHE – lhc
XENAPP – xa
XENDESKTOP – xd
XENAPP/XENDESKTOP – xad
WINDOWS – win
VIRTUAL DELIVERY AGENT – vda
HIGH DEFINITION EXPERIENCE – hdx
VIRTUAL DESKTOP – vd
CUSTOMER EXPERIENCE IMPROVEMENT PROGRAM – ceip
VIRTUAL APPS – va
DATA TRANSPORT LAYER – edt
FIREWALL – f/w
ACCESS CONTROL LISTS – acl
ADVANCED MICRO DEVICE – amd
What’s New
A full and complete list of what’s new is avaiable at – http://docs.citrix.com/en-us/xenapp-and-xendesktop/7-13/whats-new.html. I’ll start with one of my Citrix passions which is any and everything surrounding HDX technologies.
1. HDX Adaptive Transport is disabled by default in XAD 7.13* also referred to as EDT is a new HDX graphics mode that utilises both the UDP and TCP protocols with a fallback to TCP where UDP isn’t available. The HDX engineering team have engineered this new Citrix protocol called Enlightened Data Transport (EDT) which utilises the existing Citrix ports 1494 (ICA/HDX) and 2598 (Session Reliability) for both TCP and now new UDP so f/w ACL changes are near enough straight forward. To test this new graphics mode internally:
– Configure the ACL between your test end-point and through your internal network (over a VPN) VM running the 7.13 VDA to allow UDP and TCP for 1494, 2598
– Your test VM instance could be running in Azure (connected on-prem via a VPN) or on XenServer 7.1 and remember must be running the latest desktop or server VDA
– Your test end-point must be running the following min Citrix Receiver versions for Windows 4.7, Mac 12.4 and for iOS 7.2
– *In Studio create a machine catalogue, delivery group or use an existing one with your VDA upgraded from e.g 7.12 to 7.13 and then create a new HDX policy e.g HDX-TestofEDT and select the following HDX policy entitled “” and choose “Preferred“.
2. AMD Multiuser GPU (MxGPU e.g GPU Virtualization works with vSphere only) on the AMD FirePro S-series server cards for HDX 3D Pro workloads only e.g Desktop OSes ref – http://docs.citrix.com/en-us/xenapp-and-xendesktop/7-13/hdx/gpu-acceleration-desktop.html+ with support for up to 6 monitors, custom blanking & resolution, high frame rate and only GPU Pass-through is supported on the following hypervisors XenServer and Hyper-V. For further details please ref to the AMD website at – http://www.amd.com/en-us/solutions/professional/virtualization.
3. Intel Iris Pro (5-6th Gen Intel Xeon Processor E3) graphics processors supports H.264 h/w encoding for virtual apps & desktops, HDX 3D Pro support for up to 3x monitors (Ref to install options+), custom blanking & resolution, high frame rate. For further details and compatible Intel processors ref to – http://www.intel.com/content/www/us/en/servers/data-center-graphics.html
4. Other HDX enhancements include:
– Bidirectional content redirection – http://docs.citrix.com/en-us/xenapp-and-xendesktop/7-13/policies/reference/ica-policy-settings/bidirectional-content-redirection.html
– Wacom tablets improvements & connection methods – http://docs.citrix.com/en-us/xenapp-and-xendesktop/7-13/hdx/usb.html and also see http://docs.citrix.com/en-us/xenapp-and-xendesktop/7-13/policies/reference/ica-policy-settings/usb-devices-policy-settings.html
– File copying performance enhancements for client drive mapping
5. StoreFront 3.9 support for the following below and for a closer look check out the following CTX blog article – https://www.citrix.com/blogs/2017/02/24/whats-new-in-storefront-3-9/
– HDX Adaptive Display
– CEIP automatic enrollment by default. To disable please ref to http://docs.citrix.com/en-us/storefront/3-9/install-standard.html#par_anchortitle_8ea6
– Importing of NUG configurations (ZIP file or via PowerShell) into StoreFront to setup through the XAD Wizard using the latest NetScaler UG 11.1.51.21+ ref – http://docs.citrix.com/en-us/storefront/3-9/integrate-with-netscaler-and-netscaler-gateway/import-netscaler-gateway.html to reduce and avoid misconfigurations.
– Not new but if you’re looking to security harden your StoreFront standalone or cluster ref to – http://docs.citrix.com/en-us/storefront/3-9/secure.html
– SAML auth through against your preferred Store with NetScaler Unified Gateway configured as your IdP – http://docs.citrix.com/en-us/storefront/3-9/configure-authentication-and-delegation/configure-authentication-service.html#par_anchortitle_d712
5. The Connection Quality Indicator is not part of the XAD 7.13 release but an invaluable Citrix tool for Citrix SysAdmins check out its capabilities at – https://www.citrix.com/blogs/2017/02/22/citrix-connection-is-slow-not-really/ and you can download it from – https://support.citrix.com/article/CTX220774 and it also inclues group policies for better SysAdmin controls to enable or disable the tool which is supported from XAD 7.6 LTSR and upwards ref the CTX220774 article. The below image is taken from a Window 10 virtual desktop powered by XenDesktop 7.x.

6. Linux Seamless published applications from a Linux supported OS using the 7.13 VDA – http://docs.citrix.com/en-us/linux-virtual-delivery-agent/7-13/whats-new.html and also please read the publishing apps for Linux at – http://docs.citrix.com/en-us/linux-virtual-delivery-agent/1-4/suse/configuring/publish-apps.html for advanced tips and guidance on seamless mode vs. window manger configuration.
7. LHC in 7.13 introduces a new support feature for brokering operations for Citrix Cloud when the internet connection between the Citrix Cloud Connector and the Citrix Cloud control plane at – https://citrix.cloud.com/ is in a failed state or unavailable due to an ISP outage. You can also force an outage following the documentation available at – http://docs.citrix.com/en-us/xenapp-and-xendesktop/7-13/manage-deployment/local-host-cache.html++ by creating and manually modifying the following registry entry “HKLM\Software\Citrix\DesktopServer\LHC with entry of OutageModeForced” set to the value in the documentation++ to force an outage for testing and or evaluation purposes prior to implmenting Local Host Cache. I’ve embedded below a simple architectural recap of LHC introdcued in XAD 7.12 and you can read in more depth detail about Local Host Cache from a previous blog post available at – http://axendatacentre.com/blog/2016/12/13/whats-new-in-xenapp-xendesktop-7-12/.
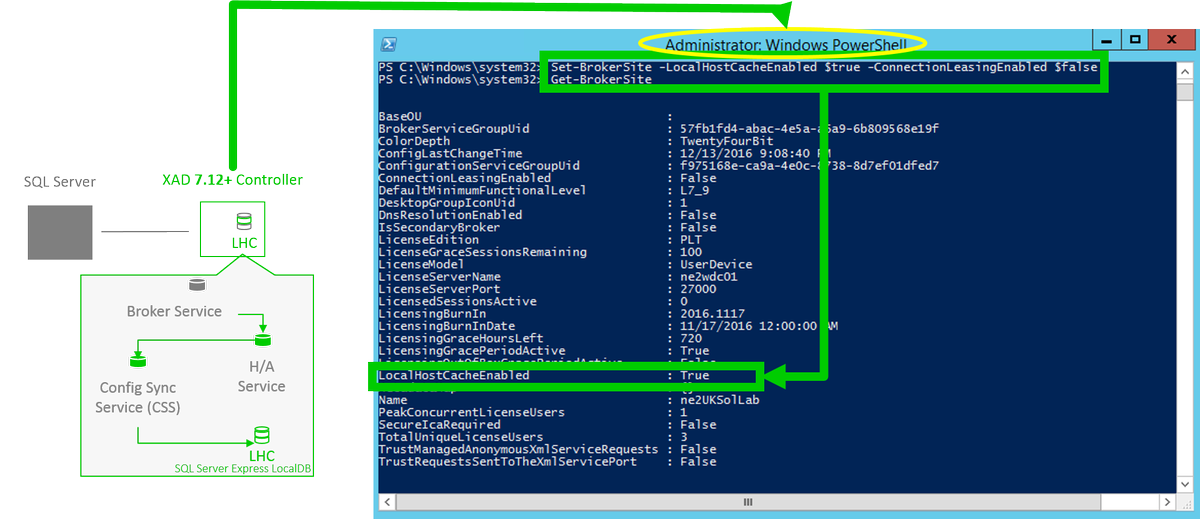
Finally LHC still provides support for brokering operations for traditional XAD Controller Site Database on-prem ref ++. I’d also recommend that you watch this TechTalks To Go covering LHC in XAD 7.12 release.
8. Provisioning Services 7.13 now supports Linux streaming and a brand new caching technique only available and supported on XenServer 7.1 called PVS-Accelerator. Check the following YouTube video from Citrix entitled “Introducing PVS-Accelerator, only available with XenServer!” via https://twitter.com/juancitrix/status/835202277317148672.
9. HDX Thinwire enhancements in 7.13 have resulted in up to 60% bandwidth savings. Take a look at the following CTX blog post at – https://www.citrix.com/blogs/2017/01/11/hdx-next-cuts-bandwidth-by-up-to-60-yes-sixty-percent/ which has some great high level LoginVSI 4.1.6 graphics comparing Thinwire in 7.12 vs. 7.13 on Windows Server 2012 R2 and 2016.
10. AppDNA what’s new ref – http://docs.citrix.com/en-us/dna/7-13/whats-new.html now includes support for Windows 10 Anniversary Update (AU) and now defaultor analysis and reporting, Secure Web reports and finally improved importing to process to analysis OSes and apps. There are a few more to be sure to check out the whats news!
Deploying XenApp 7.13 for Evaluation & Testing Purposes
The fastest way to deploy and test the latest new features from Citrix XA 7.13 release with little to no effort is to deploy the “Citrix XenApp 7.13 Trial” from Microsoft Azure available and accessiable at – https://azuremarketplace.microsoft.com/en-us/marketplace/apps/citrix.citrix-xa?tab=Overview.
Trial up to 30 days of #Citrix @XenApp 7.13 today with ease in #Microsoft @Azure – https://t.co/0DnKb5k4TO pic.twitter.com/h9L75QbnJO
— Lyndon-Jon Martin (@lyndonjonmartin) March 4, 2017
Removed from XenApp and XenDesktop 7.13
Please be sure to read and review the complete removed features and future removal features within XAD 7.x platform topics on Azure Classic, AppDisks, Desktop OS support and supported HDX Graphics Modes e.t.c –
https://docs.citrix.com/en-us/xenapp-and-xendesktop/7-13/whats-new/removed-features.html.
Viso Stencils from Citrix’s Ask the Architect – https://twitter.com/djfeller for XenApp and XenDesktop 7.13.

Image credit: https://twitter.com/djfeller/status/836557405173477376
https://virtualfeller.com/2017/02/28/visioxenappxendesktop713/
Deploying & Understanding the NetScaler Gateway Service from Citrix Cloud
The following content is a brief and unofficial prerequisites guide to better understand NetScaler Gateway Service from Citrix Cloud test delivering virtual apps and desktops powered by XenApp & XenDesktop Service prior to deploying in a PoC, Pilot or Production environment by the author of this entry. The views, opinions and concepts expressed are those by the author of this entry only and do not necessarily conform to industry descriptions or best practises. The views expressed here are my own and do not necessarily reflect the views of Citrix.
Shortened Names
NETSCALER GATEWAY SERVICE – nsg service or ngs
CITRIX CLOUD CONNECTOR – connector
NETSCALER – ns
HIGH-AVAILABILITY – h/a
XENAPP – xa
XENDESKTOP – xd
XENAPP/XENDESKTOP – xad
VIRTUAL DELIVERY AGENT – vda
HIGH DEFINITION EXPERIENCE – hdx
CITRIX CLOUD – cc
INFRASTRUCTURE AS A SERVICE – iaas
VIRTUAL APPLIANCE – vpx
USER EXPERIENCE – ux
ICA PROXY – hdx proxy
Introduction & Overview
The NetScaler Gateway Service is a simple, clean. effortless and but most importantly a powerful way to demonstrate the power of Citrix Cloud by providing secure remote access to your HDX virtual apps and desktops from your resources location over the internet (https) securely. While this service is very very powerful & simple to implement and use, you should under the keep in-mind that NS VPX/MPX/SDX is fully featured vs. the NSG Service which is focused on delivery of HDX virtual apps & desktops! So in summary when implementing service undering what is right vs. relevant for the customer needs and requirements is very important. Finally you can read more about the service and its benefits at https://www.citrix.com/products/citrix-cloud/services.html.
+Enabling the NetScaler Gateway Service
1. Login to https://citrix.cloud.com
2. Select to Manage your XAD Service which will take you to https://xenapp.cloud.com/.
3. Select from the drop down menu “Service Delivery” which is beneath the top menu item displayed “Service Creation”
4. Now Select to toggle “ON” and choose to use the NSG service (preferred for blog article only) or your own NetScaler (Unified) Gateway at your resource location and if you enable to the NSG Service you can choose to check the session reliability (2598) checkbox.
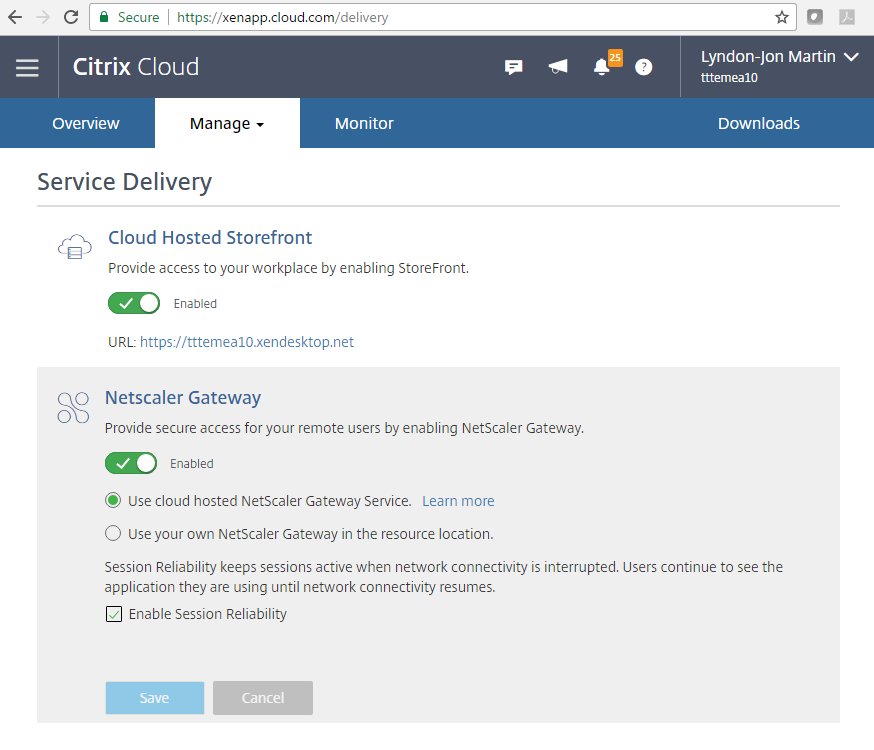
The UX
Users connect to https://
HDX Traffic flow of the NSG Service
Please note that traffic flow is based upon the diagram avaiable at – http://docs.citrix.com/en-us/citrix-cloud/xenapp-and-xendesktop-service/netscaler-gateway-as-a-service.html as of Jan 2017.
1. User MUST login into cloud hosted StoreFront e.g https://
2. Once the user has authenticated successfully he/she can select to launch a virtual app or desktop.
3. User connects to the NSG Service powered by Citrix Cloud
4. Traffic is securely brokered to the Connector in your resource location that is severing up the user’s selected virtual app or desktop or both from the server or desktop VDA.
Tech Overview of the NSG Service
1. The Citrix Cloud NetScaler Cloud Gateway service on your Connector allows and provides the secure remote access feature of the NSG Service from your chosen resource location. I have written a blog article about the Connector services and leading best practises which you can read at – http://axendatacentre.com/blog/2017/01/27/understanding-the-citrix-cloud-its-services-architecture-connectors/.
2. To ensure high availability you should always deploy at a min a pair of Connectors within your resource location and increase the compute capacity of your Connectors as user demand increases initially and thereafter deploy another Connector based upon usage of service.
3. *To use the NSG Service you MUST configure to use the cloud-hosted StoreFront provided by Citrix Cloud under “Service Delivery” tab at https://xenapp.cloud.com/delivery.
4. The NSG Service only supports HDX Traffic only and the service is currently only available on Eastern, Western coasts within the USA and in Europe so for those users accessing virtual apps and desktops via the NSG Service outside of these geos or not in close proximity to an entry point will experience higher latency so tweak your HDX policy(s)+ accordingly or deploy a NS VPX in your resource location.
5. ICA files are STA signed the below example is a small snippet from my own PoC and testing*. I have also intentionally scrammed some of the unreliable text to :-).
| Sample ICA file |
|
My Azure vDesktop $S19-38] Address=;40;CWSSTA;9D09CE5552BDE4581E888CD87EEEEFC AutologonAllowed=ON BrowserProtocol=HTTPonTCP CGPSecurityTicket=On ClearPassword=5FFE184444B0A0 ClientAudio=On ConnectionBar=1 DesiredColor=8 DesiredHRES=4294967295 DesiredVRES=4294967295 DesktopRestartAllowed=1 Domain=\78034E8888586B61 |
The NSG Service currently does not support and or is limited as of writing this blog article in Jan 2017 and based upon the embedded Twitter image – http://docs.citrix.com/en-us/citrix-cloud/xenapp-and-xendesktop-service/netscaler-gateway-as-a-service.html. Finally please remember that Citrix Cloud is consistently been updated and upgraded with new feature so please please refer to the online documentation and the service overview of Citrix Cloud even a day after posting the blog article as it may become out of date! You’ve been warned!
6. No support for Unified experiences (e.g Branding with your logo, colour scheme).
7. No support for Two Factor Authentication.
8. No support for authentication via outbound proxies for access outside of the resource location over the internet.
Citrix Cloud – NetScaler Gateway Service (NGS) Offering
You can find out more about the NGS subscription options which is avaiable at – https://www.citrix.com/products/citrix-cloud/subscriptions.html#tab-41499 and the service overview at – https://www.citrix.com/products/citrix-cloud/services.html#tab-23235
